welcome
|
|||||||||||||||||||||||||||||||||||||
Big Brother/Sis And Surveillance Systems**Please Give Page Time To Load** There are over 30 million closed-circuit television cameras in America recording 24-7, catching the average citizen on film nearly 200 times daily. Every American has a 9-digit government Social Security number assigned to them at birth. We require government licenses to drive, to get married, and have pets, government passports to travel, and corporate credit cards to book tickets, make reservations, and shop online. Our phone lines are tapped and our emails are compiled and saved. Intelligence agencies and corporations share and maintain huge databases full of information on every citizen. The government, corporate, and media interests have all melded into one cohesive unit, propagating the “official” version of reality through every newspaper and TV set.
The Information-Industrial Complex corbettreport Half a century ago, outgoing President Dwight D. Eisenhower coined the term "military-industrial
complex" to describe the fascistic collusion between the Pentagon and America's burgeoning armaments industry. But
in our day and age we are witnessing the rise of a new collusion, one between the Pentagon and the tech industry
that it helped to seed, that is committed to waging a covert war against people the world over. Now, in the 21st
century, it is time to give this new threat a name: the information-industrial complex. LINKS: Transhumanism And The Technocratic Era
The 5G Dragnet corbettreport TRANSCRIPT AND SOURCES: https://www.corbettreport.com/5g/ Telecom companies are currently scrambling to implement fifth-generation cellular network technology. But the world of 5G is a world where all objects are wired and constantly communicating data to one another. The dark truth is that the development of 5G networks and the various networked products that they will give rise to in the global smart city infrastructure, represent the greatest threat to freedom in the history of humanity.
Bilderberg and the Digital New World Order Truthstream Media Please help support us on Patreon, read our goals here: https://www.patreon.com/truthstreammedia Truthstream Can Be Found Here: LINK: Bilderberg Group
The Secrets of Silicon Valley: corbettreport TRANSCRIPT AND SOURCES: https://www.corbettreport.com/silicon... Once a sleepy farming region, Silicon Valley is now the hub of a global industry that is transforming the economy, shaping our political discourse, and changing the very nature of our society. So what happened? How did this remarkable change take place? Why is this area the epicenter of this transformation? Discover the dark secrets behind the real history of Silicon Valley and the Big Tech giants in this important edition of The Corbett Report.
***BACKGROUND REFERENCE***
Technocracy is a replacement economic system for Capitalism and Free Enterprise, and is represented by the United Nations’ program for Sustainable Development and “Green Economy.” It proposes that all means of production and consumption would be controlled by an elite group of scientists and engineers (technocrats) for the good of mankind. Technocracy was originally architected in the 1930s but regained favor when adopted by the Trilateral Commission in 1973, under their “New International Economic Order” program. https://www.technocracy.news/faq-2/
The Roots of Technocracy with Expert Patrick M. Wood Alex welcomes to the broadcast The August Forecast & Review Editor Patrick M. Wood to discuss
how the global elite within the Trilateral Commission are replacing capitalism with their own technocracy in
order to create a New International Economic Order.
MORE:
[ !! A MUST-SEE !! ] What's Your Social Credit Score? Truthstream Media | First published at 22:05 UTC on December 27th, 2019. Please help support us on Patreon, read our goals here: https://www.patreon.com/truthstreammedia Truthstream Can Be Found Here: Our Film: TheMindsofMen.net | Site: http://TruthstreamMedia.com
New surveillance cameras will use computer eyes to find 'pre crimes' by detecting suspicious behaviour and calling for guards
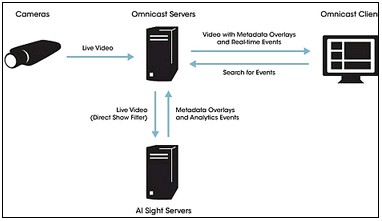
By Rob Waugh PUBLISHED: 08:12 EST, 5 June 2012 | UPDATED: 08:12 EST, 5 June 2012 A new generation of computerised 'Big Brother’ cameras are able to spot if you are a terrorist or a criminal - before you even commit a crime. The devices are installed in places like train stations or public buildings where they scan passers by to see if they are acting suspiciously. Using a range of in-built parameters of what is ‘normal’ the cameras then send a text message to a human guard to issue an alert - or call them.
Surveillance: The new BRS Labs AISight software is used with devices are installed in places like train stations or public buildings where they scan passers by to see if they are acting suspiciously Manufacturers BRS Labs said it has installed the cameras at tourist attractions, government buildings and military bases in the U.S. But the Texas-based company has offices in London, Sao Paulo, and Barcelona - meaning they could be in dozens of places around the world. In its latest project BRS Labs is to install its devices on the transport system in San Francisco,
which includes buses, trams and subways. Phone-controlled robotic submarine turns anyone into a hi-def Jacques Cousteau The company says will put them in 12 stations with up to 22 cameras in each, bringing the total number to 288. The cameras will be able to track up to 150 people at a time in real time and will gradually build up a ‘memory’ of suspicious behaviour to work out what is suspicious.
Tom Cruise in Minority Report, which also dealt with 'pre crimes': Manufacturers BRS Labs said it has installed the cameras at tourist attractions, government buildings and military bases in the U.S. The AISight system: Each camera has a series of virtual ¿trip wires¿ and if any activated then an alert is sent out to a human supervisor BRS Labs said the cameras effective have ‘the capability to learn from what they observe’. Its advanced features also mean it can compensate for poor light or a shaky image, further reducing the need for human supervision. Each camera has a series of virtual ‘trip wires’ and if any activated then an alert is sent out to a human supervisor. The relevant clip of footage is then sent over the Internet to human employees, along with a text message informing them of more details. Speaking to Fast Company, BRS Labs President John Frazzini said its technology involves 11 patents which deal with helping the machines to learn.
In the post 9/11 world, Western countries have increasingly looked to behaviour monitoring to stop themselves becoming the victims of a terrorist attack. In the UK staff at airports have been trained in ‘behavioural detection’ to spot somebody acting
suspiciously. Read more:
http://www.dailymail.co.uk/sciencetech/article-2154861/U-S-surveillance-cameras-use-eyes-pre-crimes-detecting-suspicious-behaviour-alerting-guards.html#ixzz2ezs9CzhO
Street Surveillance Is Here, LED Light Spies
**A MUST-SEE** Glenn Greenwald "The Goal Of The U.S.
Government
Mastering The Human Domain
A closer look at the upcoming Jade Helm military exercise, specifically its “master the human domain” motto, reveals a larger agenda in regards to domestic policy. ...“They’re building an infrastructure of tyranny,” stated Infowars David Knight. “There’s a legal infrastructure with things like the NDAA, there’s a technical infrastructure with things like the capability to do dragnet surveillance, and then of course there is going to be a military and law enforcement infrastructure, and those are merging.”
Synopsis
Full Presentation
LINK: TOTAL POPULATION CONTROL
Israel Hacking the World Know More News Know More News with Adam Green Support Know More News! Follow me on Social Media:
Know More News Know More News with Adam Green
Benjamin Netanyahu's Know More News Know More News with Adam Green Support Know More News! Follow me on Social Media:
Israel's Tech
Know More News Premiered May 22, 2019 Know More News with Adam Green https://www.KnowMoreNews.org/ Support Know More News! Paypal Donations - https://www.paypal.me/KnowMoreNews Patreon - https://www.patreon.com/AdamGreen Venmo - @Know-More-News Know More News Know More News with Adam Green Support Know More News! Paypal Donations - https://www.paypal.me/KnowMoreNews Patreon - https://www.patreon.com/AdamGreen Venmo - @Know-More-News
Know More News Guest Link: Know More News with Adam Green
Adam Green's Documentary can be seen here: Subverting The Public LINK: INTERNET FALSE FLAGS
NSA Records MILLIONS of Webcam Feeds & Scans
NSA Spies on MILLIONS of Webcams, Scanning People with Facial Recognition to ID Them
You Read It Here First: Government
Spies On Innocent People Via Webcams, Latest Snowden Leak confirms story Infowars Steve Watson The latest revelation concerning mass government spying confirms an issue that Infowars has been covering for close to a decade. British and American governments are spying on people in their own homes via web cams, laptop microphones and devices such as the X-box. The London Guardian has the details in a report based on information leaked by NSA whistleblower Edward Snowden. The British surveillance agency GCHQ, with help from the NSA, actively spied on nearly 2 million Yahoo users via webcams built into their computers. The documents show that the agency intercepted millions of images as part of a secret program codenamed OPTIC NERVE. The report also states that Americans were almost certainly targeted as part of the bulk collection of data, and that there is no law to prevent such activity in Britain.
The documents show that images were collected from webcams at regular intervals, one image every five minutes, and were used by the spy agency to trial automated facial recognition programs. The Guardian describes the process as “eerily reminiscent of the telescreens evoked in George Orwell’s 1984.”
The documents dub the practice as “bulk access to Yahoo webcam images/events”, and spies working at GCHQ compared it to a police database of mugshots. “Face detection has the potential to aid selection of useful images for ‘mugshots’ or even for face recognition by assessing the angle of the face,” the papers read. “The best images are ones where the person is facing the camera with their face upright.” Essentially, the spy agency appear to have been building a huge digital database containing the faces of Yahoo users. The documents advise employees at GCHQ on how to use the system, noting “[I]f you search for similar IDs to your target, you will be able to request automatic comparison of the face in the similar IDs to those in your target’s ID”. In one presentation contained within the documents, more technologically advanced systems, such as iris recognition cameras, are discussed as potential surveillance tools. The paper even chillingly states “think Tom Cruise in Minority Report”. The documents state that Yahoo users were specifically singled out because “Yahoo webcam is known to be used by GCHQ targets”. The papers also note that a large quantity of the data collected contained nudity or sexually explicit imagery. The spy agency seemingly made no effort to prevent the collection of such images. Yahoo described the practice as “a whole new level of violation of our users’ privacy,” and strenuously denied having any knowledge of the program. Infowars first reported in 2006, EIGHT YEARS AGO, that innocent people were being spied on through their computers. We specifically described the practice as Minority Report style technology, as the GCHQ had done. We have since covered the issue consistently, warning that “Hundreds of millions of Internet-active Americans will all be potential targets for secret surveillance.” Of course, some quarters dismissed our reports as “conspiracy theories”, while worried internet users questioned whether the reports were accurate. The GCHQ program was seemingly not limited to Yahoo user web cams either. Another presentation within the leaked internal papers discusses the capabilities of the Xbox 360′s Kinect camera, saying it generated “fairly normal webcam traffic” and that it was being evaluated as a potential surveillance tool. We have also documented the potential use of Xbox for surveillance purposes, noting that Skype calls made on the devices can be intercepted. We have also warned that the ‘always on’ camera of the new Xbox One, which is so powerful it can see through clothing, is wide open to abuse by hackers and government agencies. According to the leaked documents, the OPTIC NERVE program began as a prototype in 2008 and was still active in 2012. There is no indication that the program has been deactivated. Security expert Bruce Schneier writes that this latest revelation highlights how there is no distinction between actively spying on a person and what he called “Eavesdropping by algorithm”, in other words, automated computer surveillance. The NSA and the Obama administration have attempted to argue that what they are doing cannot be called “spying” or even “collecting” data, because when the data is gathered, a person is not looking at it. Director of National Intelligence James Clapper still uses this explanation to claim he never lied to Congress when he answered ‘no’ to the question “Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?” The fallout from the OPTIC NERVE program, the creation of facial recognition databases, and the fact that spooks provably looked at images of people, even NAKED images of people, highlights the fact, Schneier argues, that the “NSA’s definition of ‘collect’ makes no sense whatsoever”, and that our governments are indeed actively spying on us. —————————————————————- Steve Watson is the London based writer and editor for Alex Jones’ Infowars.com, and Prisonplanet.com. He has a Masters Degree in International Relations from the School of Politics at The University of Nottingham, and a Bachelor Of Arts Degree in Literature and Creative Writing from Nottingham Trent University. This article was posted: Thursday, February 27, 2014 at 11:18 am Tags: big brother, domestic spying
Google Becoming The Eye of Sauron
Google Hails Age of Cyber War & Digital Revolution Current executive chairman and former CEO of Google, Eric Schmidt, discusses in his new
book 'The New Digital Age: Reshaping the Future of People, Nations and Business', co-written with Jared Cohen,
that the coming digital era will be marked by military cyber-warfare, digitally-driven revolutions (as seen in
recent wave of Arab Spring uprisings), total surveillance, (online and in the physical world), and the end of
the "delete" button, meaning that privacy will be replaced by a permanent activity footprint tracked on a
database.
Google's Plan to Track You Like Cattle
Your House Is Spying On You
Military Industrial Complex has declared war on AMERICA
Next month the Federal Aviation Administration will be proposing new rules to make it easier for law enforcement agencies to have permission to use predator drones on American citizens. In the past decade the Pentagon's unmanned predator drones went from 50 to 7,000. Many fear the use of these drones on Americans are infringing on their civil liberties. Alex Jones, radio show host, joins us to look deeper into why predator drones are flying domestically. LINKS: Yes Your Government Can Use Armed Drones Against You
DHS Street Lights
In tonight's Wednesday, November 9, 2011 broadcast of the Infowars Nightly News, Alex Jones will address the launch of the nationally-coordinated Emergency Alert System takeover, which was tested earlier today on radio and television. The feds admittedly aim to expand these forced-alerts to mobile phones and the Internet as well.
EVERYTHING IS SPYING ON YOU
In this upload I read from a Prisonplanet.com article written by Paul Joseph Watson which details how the modern day police state control grid, is a high tech surveillance system of total control. The vast majority of people have no idea that most home appliances have been built to control, track and trace them.
Intellistreets COMMERCIAL
BIG BROTHER will be SPYING on you everwhere you go. INTELLISTREETS being installed in U.S.
Las Vegas Installs “Intellistreets” Light Fixtures Capable Of Recording Conversations
Mikael Thalen The Las Vegas Public Works Department has begun testing a newly installed street light system around City Hall with wide-ranging capabilities including audio and video recording.
[vid]
According to the Michigan based “Illuminating Concepts,” the system’s main benefits include “energy management, security and entertainment.” The Las Vegas setup includes such features as emergency notification flashers, playable music and a sound announcement system, all controlled from an Ipad. “Actually, there’s a server that’s housed by the company that’s providing this product and we’re communicating with just a wireless, wi-fi connection,” Neil Rohleder of the Public Works Department told My News 3. The company’s lights, which also offer a “Homeland Security” feature, received major backlash in 2011 following reports of the system’s federally-funded roll out across the country. The feature allows for emergency government announcements which will likely include such slogans as “See Something, Say Something” as well as other irrationally fear-based messages already seen in Wal Mart’s DHS-run “telescreens.” Local privacy advocate Daphne Lee has begun speaking out against the system, pointing to the ever-increasing surveillance dragnet cast over everyday innocent Americans. “This technology, you know is taking us to a place where, you know, you’ll essentially be monitored from the moment you leave your home till the moment you get home,” said Lee. The Public Works Department claims they have no plans to use the system’s surveillance cameras… for now, leading many to believe the plan is already well underway as city-wide implementation is discussed. “Right now our intention is not to have any cameras or recording devices…it’s just to provide output out there, not to get any feed or video feed coming back,” said Public Works Director, Jorge Servantes. In light of the TrapWire system, a sophisticated program that uses advanced facial recognition software through regular CCTV surveillance cameras across the country, the likelihood of the city’s cameras being covertly used by the federal government, or with permission, remains a likely outcome. Talking street lights have already been implemented in parts of Europe for a number of years. Apartment residents in North London were shocked to discover cameras ordering them to stay away from their communal garden, warning them that their photograph was being taken for entering a “restricted area.” “At what point do we say this is the land of the free? People have a right to a reasonable amount of privacy,” Lee added. As new NSA revelations widen the general public’s understanding of just how pervasive the surveillance state has become, the real question lies in whether or not the public will demand accountability as well as their privacy rights. Originally appeared at Story Leak. FLASHBACK: New Street Lights To Have “Homeland Security” Applications FLASHBACK: Talking Surveillance Cameras Coming to U.S. Streets This article was posted: Saturday, November 9, 2013 at 4:40 pm Tags: big brother, domestic spying
Company Admits New ‘Smart’ Street Lights Can Analyze Voices, Track People To aid Homeland Security in “protecting its citizens”
Paul Joseph Watson The company behind a new ‘smart’ street lighting system which is being rolled out in major cities like Las Vegas admits that the technology has the capability of analyzing voices and tracking people, features that will aid the Department of Homeland Security in “protecting its citizens.” We first reported on Intellistreets bragging of its product’s “homeland security” applications back in 2011, with the backlash from privacy advocates causing the company to remove a promotional video from YouTube. The video was later restored (see above), although comments were disabled. However, Illuminating Concepts, the company behind Intellistreets, seems to be more comfortable in acknowledging the “security” aspects of its devices now that it has secured numerous lucrative government contracts to supply street lighting in several major cities. A page on the Intellistreets website which highlights “benefits and applications” features a section on security wherein it is admitted that the hi-tech system includes “voice stress analyzers,” amongst several other sophisticated sensors that “assist DHS in protecting its citizens and natural resources.” The ability to record street conversations is merely one special feature of the Intellistreets lighting system, which is linked back to a central data hub via a ubiquitous wi-fi connection. The ‘smart’ street lights can also act as surveillance cameras, make loudspeaker security announcements (See Something, Say Something), as well as track “RFID equipped staff,” which could be any of us given the increasing amount of clothing and products which are RFID tagged. The company’s website highlights how the system is now being installed in areas of Las Vegas, Chicago, Detroit, Auburn Hills, Asbury Park, and at stadiums like the Mercedes Benz Superdome in New Orleans. As we reported on Sunday, the Las Vegas Public Works Department has begun testing the devices although they denied they would be used for surveillance, at least for the time being. Authorities in New York City also recently announced that they would be replacing the city’s 250,000 street lights with new LEDs by 2017, although it is not known how many of these if any will be provided by Intellistreets. As we reported earlier, Intellistreets are just one component of a huge network of microphones embedded in everything from games consoles to gunshot detectors that are beginning to blanket our streets and dominate our home life. A 2012 New York Times report on ShotSpotter audio sensors, which are installed in at least 70 major US cities, acknowledged that they can and have been used to record conversations on the street. The next level of NSA snooping, which will rely on systems like Intellistreets to record people’s conversations and detect antagonism or political extremism, will make the recent revelations of whistleblower Edward Snowden pale in comparison, and represents the potential for a ubiquitous wiretapping system that outstrips George Orwell’s worst nightmare. Facebook @ https://www.facebook.com/paul.j.watson.71 ********************* Paul Joseph Watson is the editor and writer for Infowars.com and Prison Planet.com. He is the author of Order Out Of Chaos. Watson is also a host for Infowars Nightly News. This article was posted: Monday, November 11, 2013 at 3:05 pm
Feds Deploy National Spy System of Microphones Capable of Recording Conversations Hidden in plain sight: The next level of NSA snooping will detect dissent via ubiquitous audio sensors
Paul Joseph Watson & Alex Jones The revelations of Edward Snowden shone fresh light on NSA spying targeting the American people, but what has gone largely unnoticed is the fact that a network of different spy systems which can record real time conversations are already in place throughout many urban areas of the United States, as well as in the technology products we buy and use on a regular basis. These systems are no secret – they are hiding in plain view – and yet concerns about the monolithic potential for their abuse have been muted. That lack of discussion represents a massive lost opportunity for the privacy community because whereas polls have shown apathy, indifference, or even support for NSA spying, anecdotal evidence suggests that people would be up in arms if they knew the content of their daily conversations were under surveillance. The dystopian movie V for Vendetta features a scene in which goons working for the totalitarian government drive down residential streets with spy technology listening to people’s conversations to detect the vehemence of criticism against the state. Such technology already exists or is rapidly being introduced through a number of different guises in America and numerous other developed countries. The Washington Post recently published a feature length article on gunshot detectors, known as ShotSpotter, which detailed how in Washington DC there are now, “at least 300 acoustic sensors across 20 square miles of the city,” microphones wrapped in a weather-proof shell that can detect the location of a sound down to a few yards and analyze the audio using a computer program. While the systems are touted as “gunshot detectors,” as the New York Times reported in May 2012, similar technology is already installed in over 70 cities around the country, and in some cases it is being used to listen to conversations. “In at least one city, New Bedford, Mass., where sensors recorded a loud street argument that accompanied a fatal shooting in December, the system has raised questions about privacy and the reach of police surveillance, even in the service of reducing gun violence,” states the report. Frank Camera, the lawyer for Jonathan Flores, a man charged with murder, complained that the technology is “opening up a whole can of worms.” “If the police are utilizing these conversations, then the issue is, where does it stop?” he said. This led the ACLU to warn that the technology could represent a clear violation of the Fourth Amendment if misused. The ACLU’s Jay Stanley asked, “whether microphones can be remotely activated by police who want to listen to nearby conversations,” noting that it was illegal for police “to make audio recordings of conversations in which they are not a participant without a warrant.” “If the courts start allowing recordings of conversations picked up by these devices to be admitted as evidence, then it will provide an additional incentive to the police to install microphones in our public spaces, over and above what is justified by the level of effectiveness the technology proves to have in pinpointing gun shots,” wrote Stanley. Eventually, if indeed it is not already happening in some major metropolitan areas, voices will be linked to biometric facial profiles via the Trapwire system, which allows the government to monitor citizens via public and private CCTV networks. As we have also previously highlighted, numerous major cities in the Unites States are currently being fitted with Intellistreets ‘smart’ street lighting systems that also have the capability of recording conversations and sending them directly to authorities via wi-fi. As we reported on Sunday, the Las Vegas Public Works Department has begun testing the devices, which act as surveillance cameras, Minority Report-style advertising hubs, and Homeland Security alert systems. As ABC 7 reported in 2011, they are “also capable of recording conversations.” Televisions, computers and cellphones are already utilizing technology that records conversations in order to bombard users with invasive targeted advertising. Last year, Verizon followed Google’s lead and officially filed a patent for a set-top box that will actively spy on Americans in their own homes by turning TVs into wiretaps. The patent application says that the technology will be capable of detecting “ambient action” including “cuddling, fighting and talking” in people’s living rooms. The box will even listen to your conversations, according to the communication giant’s patent. “If detection facility detects one or more words spoken by a user (e.g., while talking to another user within the same room or on the telephone), advertising facility may utilize the one or more words spoken by the user to search for and/or select an advertisement associated with the one or more words,” the document states. In an article we published back in 2006, we highlighted the fact that, “Digital cable TV boxes, such as Scientific Atlanta, have had secret in-built microphones inside them since their inception in the late 1990′s.” This technology is now commonplace, with products like the Xbox utilizing in-built microphones to allow voice control. Microsoft promises that it won’t use the microphones to record your conversations, which is a fairly hollow guarantee given that Microsoft collaborated with the NSA to allow the federal agency to bypass its encryption services in order to spy on people. App providers on the Android network also now require users to agree to a condition that, “Allows the app to record audio with the microphone,” on cellphones and other ‘smart’ devices. “This permission allows the app to record audio at any time without your confirmation,” states the text of the agreement.
Whistleblowers such as William Binney have warned that the NSA has virtually every US citizen under surveillance, with the ability to record all of their communications. The agency recently completed construction of a monolithic heavily fortified $2 billion facility deep in the Utah desert to process and analyze all of the information collected. If the revelations of Edward Snowden taught us one thing then it’s that if the NSA has the capability to use a technology to spy on its primary target – the American people – then it is already doing so. The state already has already had blanket access to phone records since at least 1987 under the Hemisphere program, under which AT&T gave the Drug Enforcement Agency access to call logs. This network of computer programs, urban wi-fi infrastructure and technological products inside our homes that all have the capability of recording our conversations represents an even more invasive and Orwellian prospect than anything Edward Snowden brought to light, and yet discussion of its threat to fundamental privacy has been virtually non-existent. Facebook @ https://www.facebook.com/paul.j.watson.71 ********************* Paul Joseph Watson is the editor and writer for Infowars.com and Prison Planet.com. He is the author of Order Out Of Chaos. Watson is also a host for Infowars Nightly News. This article was posted: Monday, November 11, 2013 at 11:41 am Tags: big brother, domestic spying, technology
Rand Paul “concerned about who is truly in charge of our government”
Update: Paul’s full speech can be viewed below.
Warns of “dystopian nightmares” coming true Libertarian Kentucky Senator Rand Paul warns in a speech today that he believes US spooks and shadow government agencies are ” drunk with power”, and that elected representatives are privately afraid of those operating behind the curtain. In a scheduled appearance at the University of California-Berkeley, Paul will address the continuing domestic spying controversy. In prepared comments Paul notes “I am honestly worried, concerned about who is truly in charge of our government. Most of you have read the dystopian nightmares and maybe, like me, you doubted that it could ever happen in America.” “If the CIA is spying on Congress, who exactly can or will stop them?” the comments also state. “I look into the eyes of senators and I think I see real fear. Maybe it’s just my imagination, but I think I perceive FEAR of an intelligence community drunk with power, unrepentant, and uninclined to relinquish power.”
[vid]
The Senator is set to continue on the track that saw him win CPAC’s GOP presidential nomination straw poll recently. During his CPAC speech, Paul slammed the NSA, urging “If you have a cell phone, you are under surveillance… I believe what you do on your cell phone is none of their damn business.” The Berkeley speech, which takes place at 3:30 p.m. Pacific Time, comes in the wake of the latest revelation that the NSA recorded 100% of phone calls in an unnamed foreign country, using a program dubbed MYSTIC, and a tool called RETRO — for “retrospective retrieval”. The Washington Post reported the findings yesterday, garnered from leaks by Edward Snowden. NSA documents state that the program is essentially a “time machine” that opens a door “into the past,” allowing a replay of the voices on any given call, without the need for prior identification of the person on the line. The NSA continues to argue that it is within the law for it to operate such programs in foreign countries, however, MYSTIC did not exempt US citizens living there. “Ubiquitous voice surveillance, even overseas, pulls in a great deal of content from Americans who telephone, visit, and work in the target country,” The Post reports. “Present and former U.S. officials … acknowledged that large numbers of conversations involving Americans would be gathered from the country where RETRO operates.” The report also states that the NSA has previously considered expanding the program to other countries, and may already have done so. Appearing remotely during a recent TED event, Edward Snowden declared that even bigger revelations regarding the NSA are on the way. Snowden acknowledged that every NSA spying program we are learning about now was planned before the 9/11 attacks, and that the event only served to provide justification to expand and implement more surveillance programs. Snowden said that he is concerned with exposing “one of the dangerous legacies we’ve seen in the post 9/11 era,” adding “They’re making the Internet fundamentally less safe for Americans. Is it really terrorism we’re stopping? Do these programs have any value at all? I say no. Three branches of the American government say no.” “The bottom line is terrorism has always been a cover for action—it provokes an emotional response,” he added. “The NSA asked for these authorities back in the 1990s. But Congress and the American people said no, said it’s not worth the risk to our economy. But in the post 9/11 era, they used secrecy and the justification of terrorism to start these programs in secret.”
Also appearing at the TED event was Tim Berners-Lee, one of the pioneers of the internet. Berners-Lee praised Snowden as a “hero”, while Snowden said that he supported Berners-Lee’s recent call for an Internet “Magna Carta.” “I grew up in the Internet,” Snowden said. “I believe a Magna Carta for the Internet is exactly what we need. We need to encode our values in the structure of the Internet. I invite everyone in the audience to join and participate.” Other activists seeking to battle the NSA’s domestic spying have recently targeted the new monolithic Utah data center, promoting a campaign to cut off the water supply to the facility. Because this is actually quite a good idea, and it has garnered interest from lawmakers, it has not gone unnoticed by those who are “drunk on power”, as Rand Paul describes them. The NSA is now actually arguing that its water bill should be declared top secret and that it should not need to declare how much water is being pumped into the Utah facility as a matter of national security. “By computing the water usage rate, one could ultimately determine the computing power and capabilities of the Utah Data Center,” wrote the NSA’s associate director for policy and records, David Sherman in an undated letter written in response to a request for the information from The Salt Lake Tribune. “Armed with this information, one could then deduce how much intelligence NSA is collecting and maintaining.” Sherman argues. Documents uncovered by the Tribune have indicated that the NSA facility could use between 1.2 and 1.7 MILLION gallons of water PER DAY.
Meanwhile, the Defense Department’s Inspector General, who is supposed to oversee the NSA’s activities and ensure they are within the law, admitted yesterday that he had no idea that the NSA was collecting bulk metadata on Americans’ communications. “From my own personal knowledge, those programs, in and of themselves, I was not personally aware,” Anthony C. Thomas said. Thomas also announced that the Pentagon has no intention to investigate the matter. Thomas said he was “waiting to see the information that the NSA IG (inspector General) brings forward with the investigations that are going on, and what we often do not want to do is conflict.” That is some valuable oversight from the executive branch! —————————————————————- Steve Watson is the London based writer and editor for Alex Jones’ Infowars.com, and Prisonplanet.com. He has a Masters Degree in International Relations from the School of Politics at The University of Nottingham, and a Bachelor Of Arts Degree in Literature and Creative Writing from Nottingham Trent University. This article was posted: Thursday, March 20, 2014 at 11:10 am Tags: big brother, domestic spying
Microsoft's Kinect System is Watching You
Microsoft X-Box Kinect games device has a video camera and a microphone that records speech. Microsoft has stated that users "should not expect any level of privacy concerning your use of the live communication features," and the company "may access or disclose information about you, including the content of your communications."
New Xbox Can See Through Your Clothes Like TSA Scanners System can be hacked and exploited by pervs Adan Salazar
If the successes of its past game console launches are any indicator, sales of Microsoft’s latest effort – set to hit the market November 22 – can be expected to be strong. However, this console, which seeks to be your living room’s all-in-one home entertainment unit, is immensely different from the rest.
But the most disturbing and worrisome Xbox One/Big Brother gossip is not that Xbox maker Microsoft was reportedly involved in the NSA PRISM scandal, or that the console’s Kinect peripheral sits listening with a multi-microphone array 24/7 for voice commands, or that its noise-isolation capabilities enable it to distinguish your voice among a crowd of your friends. The most startling revelation is that the new Kinect device, to be sold in combination with the XBox One, at times has the ability to map out in high-definition the shape of genitalia, something fine and dandy for consenting adults, but which could ultimately be exploited by hackers and perverts to gain access to images of children. The cameras aren’t exactly designed to scope out your man or womanhood; it just happens that way because the technology simply works too well, says Fast Company writer Mark Wilson. In viewing a demo of the new Kinect from Microsoft Research, Wilson says he noticed something unmistakable that gave him cause for concern. “… I noticed, alongside the intricacies of a hoodie and jeans–and there’s no graceful way to put this–a dong.” “The Kinect hardware/software is now so effective at deciphering the bumps and folds of clothing,” says Wilson, “that it can pinpoint a man’s package down to its pant leg, carving out the distinctive folds in our trousers that society, backed by a bit of shadowy denim, has become remarkable at ignoring.” Although it as yet unknown whether the new Xbox will be snapping or storing images, past examples of government mischief teach us to err on the side of caution. In 2010, an Orlando, Fla. federal courthouse admitted that their Brijot Gen2 millimeter wave screening device had stored “approximately 35,314 images.” On its website, Brijot confirmed their machine could store up to 40,000 images and records.
Likewise, laptops issued by a suburban Philadelphia school in 2010 were also found to be capturing “secret webcam pictures of a high school student when he was partially undressed or sleeping in his bed.” Additionally, a motion filed against the school stated that “Thousands of webcam pictures and screen shots have been taken of numerous other students in their homes…” And just last August, a hacker spouted insults at a 2-year-old girl — through her baby monitor. Indeed, every new technology is open to hackers, as evidenced in the case of Google Glass earlier this year. By this metric, it is no stretch to say the new Xbox will undoubtedly be compromised by hackers or perverts, and that this system needs to be investigated. It was already widely known that the new Kinect’s sensors would be highly invasive, but this should add a whole new level of unease for parents who buy their kids all the latest, trendiest gadgets. For instance, it was already known that the Kinect’s high-definition camera creates a model of your human skeleton and can track you moving about in your home, in addition to being able to monitor your heart rate in order to gauge your level of enjoyment. And, it was already known that the Kinect will carefully study users’ eye movements and facial expressions in order to “reward” them with meaningless “virtual rewards” like avatars, in addition to creating profiles of individuals’ likes and dislikes, allowing it to serve up customized ads, services, or shows it thinks users might like.
As Wilson notes, allowing the new Kinect into your living room is on par with inviting one of the TSA’s millimeter wave scanners or backscatter X-ray machines into your home. But in contrast to the somewhat voluntary nature of the TSA’s prying eyes, the most unnerving thing about Kinect’s genitalia-viewing potential is that the gaming market’s target audience is primarily children and most will not know they can “opt-out.” Nevertheless, Wilson approaches his find optimistically, saying “a small percentage of Xbox owners may ever have such an experience. This topographical view is essentially a debug mode (I believe, accessible to gamers, but far from standard), and most Kinect experiences will likely render you as a bubbly asexual cartoon or a character with stock anatomy, smoothing over everything from hoodie strings to the overzealous nipples.” However, anxieties over Microsoft’s alleged participation in setting up backdoors for the NSA should still leave gamers and parents wary of next generation consoles’ supposed technological advancements.
Below is the video Wilson analyzed.
This article was posted: Friday, November 15, 2013 at 3:12 pm Tags: internet, science, technology
WiTrack: 3D Motion Tracking Through Walls Using Wireless Signals The NETMIT group at MIT develops a new technology that can see through walls, performing 3D motion tracking. The technology has applications in gaming, elderly monitoring, and gesture-based user interfaces.
Pennsylvania school sued for spying on student at home
A Pennsylvania school district accused of secretly switching on laptop computer webcams inside students' homes is under investigation by federal authorities, a law enforcement official with knowledge of the case told The Associated Press. The FBI will look into whether any federal wiretap or computer-intrusion laws were violated by Lower Merion School District officials, the official, who spoke on condition of anonymity because the official was not authorized to discuss the investigation, told the AP on Friday. Days after a student filed suit over the practice, Lower Merion officials acknowledged Friday that they remotely activated webcams 42 times in the past 14 months, but only to find missing student laptops. They insist they never did so to spy on students, as the student's family claimed in the federal lawsuit. Families were not informed of the possibility the webcams might be activated in their homes without their permission in the paperwork students sign when they get the computers, district spokesman Doug Young said. "It's clear what was in place was insufficient, and that's unacceptable," Young said. The district has suspended the practice amid the lawsuit and the accompanying uproar from students, the community and privacy advocates. District officials hired outside counsel to review the past webcam activations and advise the district on related issues, Young said. Remote-activation software can be used to capture keystrokes, send commands over the Internet or turn computers into listening devices by turning on built-in microphones. People often use it for legitimate purposes -- to access computers from remote locations, for example. But hackers can use it to steal passwords and spouses to track the whereabouts of partners or lovers. The Pennsylvania case shows how even well-intentioned plans can go awry if officials fail to understand the technology and its potential consequences, privacy experts said. Compromising images from inside a student's bedroom could fall into the hands of rogue school staff or otherwise be spread across the Internet, they said.
Mindless Sheep Thumbscan To Get Into Disney World
Just look at these pathetic sheep being herded in to be thumbscanned. It makes me so sick. LINK: BIOMETRICS
Orwellian Police Device Can See Through Clothing
Orwellian Police Device Can See Through Clothing
Red Squad Back Big Brother cameras zoom in on Chicago
In what has been dubbed Operation Virtual Shield, thousands of public and privately owned security cameras have been put in place in Chicago and linked together, creating a capsule of surveillance over the entire city, more extensive than anywhere else in the United States. Chicago holds the record for number of surveillance cameras, estimated at up to 10,000. The network is said to have cost $60 million. Officials say it is worth the price, but privacy concerns are at a peak.
Street Lights Are Spying on You Intellistreets Systems Now
Talking surveillance cameras that bark orders
at passers-by and can also record conversations are heading for U.S. streets, with manufacturer Illuminating
Concepts announcing the progress of its 'Intellistreets' system.
US surveillance state
These days our surveillance state isn't only growing because of the government, but it's also thanks to the tech giants. A congressional hearing was held titled, "Protecting Mobile Privacy" but DOJ's Jason Weinstein called for new laws that would require mobile providers to collect and store information about their customers, as in less privacy, at a hearing about privacy. Cato's Julian Sanchez explains.
Shadow
Government (FULL MOVIE) In these times, weve all come to accept that our e-mails, telephone calls and financial
transactions can be monitored and tracked, but do we really know how much of our lives are actually being observed
and recorded and by whom? This reveals how we have been incrementally conditioned over the years. It should make us realise that since this pattern of events is recorded from the earlier part of the last century, how much more will we be socially engineered in 50 years from now? It includes the shocking story of how you unwittingly submit the most private and intimate details about every aspect of your life every single day. For example, imagine what a retail loyalty card reveals about you. Each time you scan it, a calculation of every item on your shopping list is done in order to reach the value of your discount voucher. This is an exact record of your weekly shopping routine, so it is predictable what you intend to purchase each week. This information is kept on a database somewhere alongside your photo, which is taken up 300 times per day. This loyalty card provides information on how many people you live with, yours and their daily household routines and lifestyles, your diet, your personal hygiene, your habits, your sex life and sexuality, your hobbies and interests, your job and much much more. Almost every electrical item in your home today has an RFID chip. The documents you printed off or the photos you scanned into your computer are all recorded. As soon as you walk out your front door, every step you take and where you go is on CCTV. Someone knows your home is empty. While you do your shopping, take a look around you. How many people can you spot who are oblivious to their own surroundings? If you accidentally bump into one of them, the chances are, they won't hear you apologize, since they are cut off from the world through the earpieces, feeding junk or hazardous information to their brains. However. You could just tell yourself that this is just paranoia, or the programmed response already in circulation, "I have nothing to hide, so I don't care". DENIAL IS THE FIRST SIGN OF SUBMISSION
Proprietary Software is an Instrument of Unjust Power
Alex welcomes back to the show software freedom activist and computer programmer Richard
Stallman who talks about a claim that scientists can hack the brain. He also talks about built-in trapdoors in
electronics manufactured in China. Stallman pioneered the concept of copyleft and he is the main author of the GNU
General Public License.
“Domestically, they’re pulling together all the data about virtually every U.S. citizen in the country and assembling that information, building communities that you have relationships with, and knowledge about you; what your activities are; what you’re doing. So the government is accumulating that kind of information about every individual person and it’s a very dangerous process.”
LINK: NSA CAUGHT SPYING ON EVERYONE!
Obama
Fears Arrest and is Running Scared From [vid] Obama is so desperate to
brush aside the governments illegal NSA spying activity that he compared it to the actions of patriot Paul
Revere.
CASHLESS Paper Currencies Are Being Destroyed By Design It should be blatantly obvious to Christians where this is going...
LINK: CASHLESS TRACKABLE SOCIETY
New Facial Recognition App Scans Crowds To Find Online Dating Profiles of Women In View
New Facial Recognition App Scans Crowds, Finds Online Dating Profiles of Women.
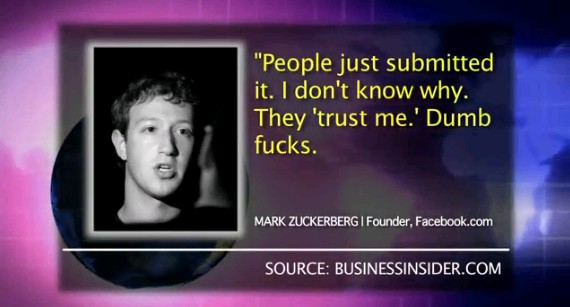
Facebook (Privacy Hater) CEO Refers to It's Users as Dumb Fucks
NWOTASER - Corbettreport — May 23, 2010 — http://www.corbettreport.com Facebook CEO Mark Zuckerberg and his company are suddenly facing a big new round of scrutiny and criticism about their cavalier attitude toward user privacy. An early instant messenger exchange Mark had with a college friend won't help put these concerns to rest. According to SAI sources, the following exchange is between a 19-year-old Mark Zuckerberg and a friend shortly after Mark launched The Facebook in his dorm room: Zuck: Yeah so if you ever need info about anyone at Harvard Zuck: Just ask. Zuck: I have over 4,000 emails, pictures, addresses, SNS [Redacted Friend's Name]: What? How'd you manage that one? Zuck: People just submitted it. Zuck: I don't know why. Zuck: They "trust me" Zuck: Dumb fucks.
LINKS:
“Secret” 3G Intel Chip Gives Snoops Backdoor PC Access
vPro processors allow remote access even when computer is turned off
Paul Joseph Watson
Intel Core vPro processors contain a “secret” 3G chip that allows remote disabling and backdoor access to any computer even when it is turned off. 
Image: Intel Core vPro. Although the technology has actually been around for a while, the attendant privacy concerns are only just being aired. The “secret” 3G chip that Intel added to its processors in 2011 caused little consternation until the NSA spying issue exploded earlier this year as a result of Edward Snowden’s revelations. In a promotional video for the technology, Intel brags that the chips actually offer enhanced security because they don’t require computers to be “powered on” and allow problems to be fixed remotely. The promo also highlights the ability for an administrator to shut down PCs remotely “even if the PC is not connected to the network,” as well as the ability to bypass hard drive encryption. “Intel actually embedded the 3G radio chip in order to enable its Anti Theft 3.0 technology. And since that technology is found on every Core i3/i5/i7 CPU after Sandy Bridge, that means a lot of CPUs, not just new vPro, might have a secret 3G connection nobody knew about until now,” reports Softpedia. Jeff Marek, director of business client engineering for Intel, acknowledged that the company’s Sandy Bridge” microprocessor, which was released in 2011, had “the ability to remotely kill and restore a lost or stolen PC via 3G.” “Core vPro processors contain a second physical processor embedded within the main processor which has it’s own operating system embedded on the chip itself,” writes Jim Stone. “As long as the power supply is available and in working condition, it can be woken up by the Core vPro processor, which runs on the system’s phantom power and is able to quietly turn individual hardware components on and access anything on them.” Although the technology is being promoted as a convenient way for IT experts to troubleshoot PC issues remotely, it also allows hackers or NSA snoops to view the entire contents of somebody’s hard drive, even when the power is off and the computer is not connected to a wi-fi network. It also allows third parties to remotely disable any computer via the “secret” 3G chip that is built into Intel’s Sandy Bridge processors. Webcams could also be remotely accessed. “This combination of hardware from Intel enables vPro access ports which operate independently of normal user operations,” reports TG Daily. “These include out-of-band communications (communications that exist outside of the scope of anything the machine might be doing through an OS or hypervisor), monitoring and altering of incoming and outgoing network traffic. In short, it operates covertly and snoops and potentially manipulates data.” Not only does this represent a privacy nightmare, it also dramatically increases the risk of industrial espionage. The ability for third parties to have remote 3G access to PCs would also allow unwanted content to be placed on somebody’s hard drive, making it easier for intelligence agencies and corrupt law enforcement bodies to frame people. “The bottom line? The Core vPro processor is the end of any pretend privacy,” writes Stone. “If you think encryption, Norton, or anything else is going to ensure your privacy, including never hooking up to the web at all, think again. There is now more than just a ghost in the machine.” Facebook @ https://www.facebook.com/paul.j.watson.71 ********************* Paul Joseph Watson is the editor and writer for Infowars.com and Prison Planet.com. He is the author of Order Out Of Chaos. Watson is also a host for Infowars Nightly News. This article was posted: Thursday, September 26, 2013 at 5:56 am Tags: big brother, domestic spying, technology
NSA Remotely Hacks Into Computers NOT CONNECTED
NSA Can Remotely Hack Into Computers NOT CONNECTED TO THE INTERNET!!!
Feds planning black box vehicle mandate to track, tax and even remotely control all personal vehicles Mike Adams The federal government is working on a plan that would mandate black box tracking devices be installed in every vehicle, with real-time uploading of vehicle location, speed and mileage to government authorities. This Orwellian technology is already technically feasible and will be promoted as a way to increase “highway safety” while boosting government revenues from mileage taxation.
“The devices, which track every mile a motorist drives and transmit that information to bureaucrats, are at the
center of a controversial attempt in Washington and state planning offices to overhaul the outdated system for
funding America’s major roads,” reports the LA Times.
“[Congress is] exploring how, over the next decade, they can move to a system in which drivers pay per mile of road they roll over. Thousands of motorists have already taken the black boxes, some of which have GPS monitoring, for a test drive.” There are three hugely important realizations to glean from all this: Realization #1) The government wants to track your every move The USA is already an admitted surveillance state. As leaked documents from Edward Snowden have revealed, the NSA openly spies on all your phone calls, text chats, web surfing behavior, bank account activity and more. (Article Continues Below Vid)
Big Brother - A Black Box In Your Car?
Now, the government wants to add real-time tracking of your vehicle location to that long list of surveillance targets. This would of course allow the government to: • Track and map all your driving trips. • Know when you are home or away from home. • Know where you work. • Establish patterns of your activity such as when you pick up kids from school or go grocery shopping. • Know if you attend political rallies, activist meetings, gun ranges or other destinations the government characterizes as being linked to “domestic terrorism.” The government could then use this information to target you for punitive tax audits, surprise armed raids, government shakedowns or other nefarious schemes that are have now been revealed as routine extortion activities carried out by a criminal government. (See video, below.) Realization #2) Government can turn EVERY road into a toll road Both state and federal governments absolutely love the idea of taxing you for every mile you drive. This fits into the “government utopia” of taxing you for breathing (carbon dioxide taxes), taxing you for working (payroll taxes) and even taxing you for dying (estate taxes). Of course, governments already indirectly tax driving by taxing fuel. If you wanted to tax driving, taxing fuel is actually a very efficient way to do it. But the rise of electric vehicles is starting to freak out governments because they don’t have a way to tax the actual road mileage of vehicles that don’t burn gasoline or diesel. Because governments inherently believe that all your money already belongs to them, they perceive electric vehicles as a source of “lost revenues.” These lost revenues diminish the power and wealth of government while also limiting the amount of money that can be awarded to wealthy donors via no-bid contracts (such as the $600 million no-bid contract to build the failed Healthcare.gov website). As a result, governments are drooling over the idea of using vehicle black boxes to tax you for every mile you drive, effectively turning every road into a toll road. Watch for this to start out as a very small tax to be more easily embraced by the public (maybe a penny per mile) and then get ratcheted up to $1, $2, or even $5 per mile in some areas. Realization #3) Two-way communication allows government to control your vehicle Black boxes don’t have to be only one-way communication devices. They can also receive commands from government authorities such as commands to: • Shut down your vehicle and disengage the starter, effectively stranding you with no way to drive. • Lock you inside your own vehicle, trapping you until “authorities” arrive. • Cause your car to drive off a cliff as a method of assassinating political enemies, then blaming it on their “bad driving.” • Cause your vehicle to run over pedestrians, thereby earning you a prison sentence for “vehicular manslaughter.” (Yet another way to dispatch political enemies.) • Through two-way black boxes, the government can even use coordinated vehicle control to do things like build a highway roadblock from 10 cars, cause a massive 50-car accident, or even drive a stream of heavy trucks through the walls of a family residence in an effort to kill a journalist. It’s no joke that two-way black boxes allow the government to turn your vehicle into a weapon while simultaneously compromising your freedom of movement. Through black boxes, governments can transform your car — once a symbol of freedom — into a rolling prison cage which may be used to imprison you, harm you or harm others. Imagine, too, what happens when hackers seize control of the government’s vehicle control system. They could then turn cars against each other and, with all the drivers trapped inside, turn America’s roadways into a deadly demolition derby… (although, it’s worth noting that most hackers actually have a greater sense of ethics than government, and the only hackers who might engage in such behavior would probably be Chinese hackers engaged in acts of war against America.) The U.S. government is now a criminal mafia extorting money from the citizenry We already know the U.S. government has become a criminal enterprise that uses extortion, intimidation, threats and even acts of violence against the American people to command their compliance. This has just been made frighteningly clear by a new book called Political Extortion by Peter Schweizer. This is a must-read book that reveals the true criminal nature of the federal government and how governments use mafia-style tactics to extort money from the public in order to fund the lavish lifestyles of bureaucrats and politicians. Watch Schweizer’s interview with Lou Dobbs here:
This article was posted: Monday, October 28, 2013 at 6:43 am Tags: domestic news, government corruption
Ford Motors “Knows Everyone Who Breaks The Law” Infowars.com In yet another push by the corporatocracy to prepare the population for mileage taxes, automatic speeding tickets and unaffordable car insurance if you choose not to purchase one of their self-driving cars, a Ford executive bragged about knowing everything about your driving but promised not to tell. It was more of a threat than a revelation since traffic data has been collected for Google maps for several years to show congestion and traffic conditions.
[vid]
This article was posted: Friday, January 10, 2014 at 6:21 am
Ford Exec: ‘We Know Everyone Who Breaks The Law’ Thanks To Our GPS In Your Car JIM EDWARDS Ford’s Global VP/Marketing and Sales, Jim Farley, said something both sinister and obvious during a panel discussion about data privacy today at CES, the big electronics trade show in Las Vegas. Because of the GPS units installed in Ford vehicles, Ford knows when its drivers are speeding, and where they are while they’re doing it.
Rather, he said, he imagined a day when the data might be used anonymously and in aggregate to help other marketers with traffic related problems. Suppose a stadium is holding an event; knowing how much traffic is making its way toward the arena might help the venue change its parking lot resources accordingly, he said. This article was posted: Thursday, January 9, 2014 at 6:36 am Tags: domestic spying, police state, technology
Navy Database Tracking Civilians: "Banana Republic" [vid]
Guilt by association for journalist who interviewed Al Qaeda, death by hacking medical devices and closing arguments in the Bradley Manning case. http://washingtonexaminer.com/navy-da... http://www.infowars.com/la-police-all... http://www.infowars.com/nsa-hacker-br... http://www.infowars.com/al-sharpton-w... http://www.infowars.com/senate-has-vo...
Shotspotter
Man arrested for firing 4 warning shots to ward off
New airport scanner tunnel (video) David Millward The 21 feet long smart tunnel combines all existing and imminent security technology in one place and would slash the time passengers wait at airports. Passengers would simply walk the length of the tunnel while they are scanned. It would prevent the frustration many passengers feel when they have to partially undress at a security gate. A version is expected to be trialled within 18 months and could be rolled out at major airports within five years. British authorities are known to be keen to use the next generation of airport security scanners as soon as possible. Fresh food that lasts from eFoods Direct (Ad) Currently the aviation industry allows 30 seconds for passengers to pass through the existing security system.
This article was posted: Wednesday, June 8, 2011 at 9:19 am
Homeland Security to Activate ‘National License Plate Recognition Database’ UK version of spy system was used to target political activists
Paul Joseph Watson
The details are included in a PDF attachment uploaded yesterday to the Federal Business Opportunities website under a solicitation entitled “National License Plate Recognition Database.” The system will “track vehicle license plate numbers that pass through cameras or are voluntarily entered into the system from a variety of sources (access control systems, asset recovery specialists, etc.) and uploaded to share with law enforcement” in order to help locate “criminal aliens and absconders.” In other countries that have activated license plate tracking networks, such as the United Kingdom, political activists have been targeted by having their vehicles added to a “hotlist” after attending protests. One example led to a man being questioned under anti-terror laws after he traveled to take part in an anti-war demonstration. As the image above illustrates, the cameras are also used by local governments in Australia to keep records of people who violate parking restrictions. Critics of the system in Australia have condemned it as “a Pandora’s box for abuse of power, mistakes and illegal disclosure,” stressing that the technology allows authorities to record “your number plate at a certain time and location,” allowing police to “compile an extraordinary amount of data about you. This includes your name, address, contact details, driving history and licence status.” “Innocent people are increasingly being treated with suspicion due to the tiny chance that some offence may be committed,” writes David Jancik. The DHS’ database will allow authorities “to determine where and when the vehicle has traveled,” using data compiled “from a variety of sources nationwide,” including “metropolitan areas” within the United States, suggesting the system may be linked in with regular surveillance cameras as it is in the UK. The system will also allow DHS officials to take a picture of any license plate via their smartphone, upload it to the database and immediately receive an alert if the plate is on the watchlist. “The NLPR data service should provide details on clarity of photos provided. The Government would prefer a close-up of the plate and a zoomed out image of the vehicle,” states the solicitation. The system must also have the capability to “flag license plates and conduct searches anonymously so that other law enforcement agencies may not have access.” Given rampant concerns that the Department of Homeland Security, which is ostensibly introducing this system in the name of catching illegal aliens, is in fact an increasingly bloated federal bureaucracy designed to target the American people, the notion of the DHS enjoying access to a fully integrated nationwide license plate tracking grid is chilling, especially given the fact that the agency has funded reports which characterize “liberty lovers” as potential terrorists. The DHS also recently awarded the Massachusetts Bay Transportation Authority $7 million dollars to outfit its buses with high tech 360 degree surveillance cameras. The federal agency is simultaneously supporting the rollout of ‘Intellistreets’ lighting systems that double as surveillance hubs which can record conversations. “Do not kid yourself. This is tracking of an individual that can be accessed at a whim,” writes James Smith. “Yearly, officers are terminated for accessing the LEDS/NCIC database for looking into the histories of ex-lovers, future spouses, and potential sons/daughters-in-law. And with license plate tracking toy (not a tool), they will know where you are, as long as you have driven into the cross hairs of this new weapon for tyranny.” Facebook @ https://www.facebook.com/paul.j.watson.71 ********************* Paul Joseph Watson is the editor and writer for Infowars.com and Prison Planet.com. He is the author of Order Out Of Chaos. Watson is also a host for Infowars Nightly News. This article was posted: Thursday, February 13, 2014 at 6:10 am Tags: big brother, domestic spying
Tattle-Tell Squads, and SurveillanceGermans under Hitler denounced their neighbors and friends not because they genuinely believed them to be a security threat, but because they expected to selfishly benefit from doing so, both financially, socially and psychologically via a pavlovian need to be rewarded by their masters for their obedience. At the height of its influence around one in seven of the East German population was an informant for the Stasi. As in Nazi Germany, the creation of an informant system was wholly centered around identifying political dissidents and those with grievances against the state, and had little or nothing to do with genuine security concerns. LINK: Tattle-Tell Squads and Surveillance
Fighting Back Against
Why are our controllers creating a surveillance society? What is the psychological agenda behind
the panopticon society? Anti Big-Brother crusader Steve Jolly tells us about the next level of digitized
micromanagement - and what you can do to fight back.
LINKS: THE TECHNOCRACY | Bread and Circus
MORE SOLUTIONS HERE: Fighting Back Against Big Brother
-- Harriet Tubman --
"I freed a thousand slaves; I
could have freed a thousand more,
Only the vigilant can maintain their liberties, and only those who
are constantly and intelligently "A society, most of whose members spend a great part of their time,
not on the spot, not here and now and in their calculable future, but somewhere else, in the irrelevant other
worlds of sport and soap opera, of mythology and metaphysical fantasy, will find it hard to resist the
encroachments of those who would manipulate and control it.” - Aldous Huxley - LINK: Bread and Circus
TOTAL SURVEILLANCE SOCIETY LINK: Transhumanism And The Technocratic Era
GO HERE TO UNDERSTAND HOW ALL THIS FITS WITHIN
REACH OUT TO OTHERS [Help Educate Family And Friends With This Page And The Links Below]
MORE: Big Brother/Sis & Surveillance Systems | The NSA (National Security Agency) | Mobile Van Radiating the Public | DRONES | Microchip Implants | India Biometrics 1.2 Billion People | National I.D. Card | Communications Takeover by EAS | Cell Phones Are Tracking Devices | SMART METERS | 10 Reasons Why Nothing You Do On The Internet Will EVER Be Private Again | CASHLESS TRACKABLE SOCIETY | Facedeals scans your face to customize deals | RFID chip Mandatory at Schools | GOOGLE GLASS | DHS SPY GRID
| |||||||||||||||||||||||||||||||||||||
























 Virtually every new technological device now being manufactured
that is linked to the Internet has the capability to record conversations and send them back to a central hub.
Is it really any wonder therefore that former CIA director
Virtually every new technological device now being manufactured
that is linked to the Internet has the capability to record conversations and send them back to a central hub.
Is it really any wonder therefore that former CIA director 

 In line with the pervading surveillance culture, where microphones and cameras
embedded within tablets, cell phones, laptops, light posts, vehicles and other devices watch and listen
intently, Microsoft is making sure to load its gaming device with the latest spy tech goodies, which they
claim will enhance users’ experiences.
In line with the pervading surveillance culture, where microphones and cameras
embedded within tablets, cell phones, laptops, light posts, vehicles and other devices watch and listen
intently, Microsoft is making sure to load its gaming device with the latest spy tech goodies, which they
claim will enhance users’ experiences.











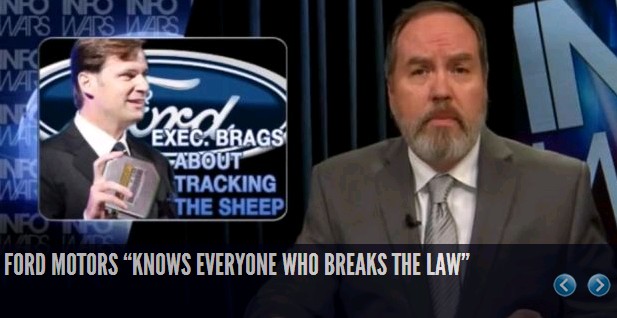
 Farley was trying to describe how much data Ford has on its customers, and illustrate
the fact that the company uses very little of it in order to avoid raising privacy concerns: “We
know everyone who breaks the law, we know when you’re doing it. We have GPS in your car, so we know what
you’re doing. By the way, we don’t supply that data to anyone,” he told attendees.
Farley was trying to describe how much data Ford has on its customers, and illustrate
the fact that the company uses very little of it in order to avoid raising privacy concerns: “We
know everyone who breaks the law, we know when you’re doing it. We have GPS in your car, so we know what
you’re doing. By the way, we don’t supply that data to anyone,” he told attendees.