welcome
|
||||||||||||||||||||||||||||||||||||||||||
Plan to Turn Post Office Trucks Into Stasi Data Collection Nodes The Pentagon's spy unit has begun rebuilding a controversial database that was shut down three years ago after it was found to have been used to monitor US peace activists. The database, named TALON, included scores of reports on nonviolent demonstrations and antiwar rallies. Targets included Quaker and church groups, organizers of "Don't Ask, Don't Tell" protests, and student activists mobilizing against the Iraq war. The Defense Intelligence Agency has filed notice it wants to effectively revive TALON and rename it Foreign Intelligence and Counterintelligence Operation Records, with the purpose of tracking terror threats. The Washington Post reports the new database will likely inherit TALON's records
Plan to Turn Post Office Trucks Into Stasi Data Collection Nodes Kurt Nimmo Forget the StreetView data vacuum scandal. If an idea proposed for the money hole known as the U.S. Post Office is adopted, your friendly neighborhood postal person may be soon driving a high-tech data collection vehicle that would rival anything Google put to use for the government. The Pentagon's spy unit has begun rebuilding a controversial database that was shut down three years ago after it was found to have been used to monitor US peace activists. The database, named TALON, included scores of reports on nonviolent demonstrations and antiwar rallies. Targets included Quaker and church groups, organizers of "Don't Ask, Don't Tell" protests, and student activists mobilizing against the Iraq war. The Defense Intelligence Agency has filed notice it wants to effectively revive TALON and rename it Foreign Intelligence and Counterintelligence Operation Records, with the purpose of tracking terror threats. The Washington Post reports the new database will likely inherit TALON's records.
“The service’s thousands of delivery vehicles have only one purpose now: to transport mail,” Michael Ravnitzky, chief counsel to the chairman of the Postal Regulatory Commission, wrote for the New York Times last week. “But what if they were fitted with sensors to collect and transmit information about weather or air pollutants? The trucks would go from being bulky tools of industrial-age communication to being on the cutting edge of 21st-century information-gathering and forecasting.” “Data collection wouldn’t require much additional staff or resources; all it would take would be a small, cheap and unobtrusive sensor package mounted on each truck,” writes Ravnitzky. He said outfitting the trucks would make “it significantly easier to spot a problem or anomaly” and the system “could assess road quality, catalog potholes and provide early warning of unsafe road conditions like black ice.” Forget the prospect of weather forecasting or black ice. The federal government is far more interested in collecting data on citizens than it is on reporting road conditions. The NSA and the CIA don’t give a hoot about potholes. On Monday, the CIA’s favorite newspaper, the Washington Post, told us what we already know – the government has created a massive Stasi-like snoop apparatus in America. “The government is creating a vast domestic spying network to collect information about Americans in the wake of the September 11, 2001 attacks and subsequent terror plots,” Reuters reported. “The government is using for this purpose the FBI, local police, state homeland security offices and military criminal investigators,” and may soon use the Post Office if Mr. Ravnitzky’s proposal is adopted. “The government’s goal is to have every state and local law enforcement agency in the country feed information to Washington to buttress the work of the FBI, which is in charge of terrorism investigations in the United States,” explains CBS News. The FBI is also in the business of setting up patsies in order to promote the manufactured war on terrorism. “Everything contained within the Post’s article has already been reported and covered in depth by this website and others in the alternative media that have consistently warned of the threat of the exponential rise of the big brother spy system over the past decade,” writes Steve Watson. “The Washington Post report notes that such suspicious activity reports are just one piece of information being collected at the local and state levels and fed into a vast ‘Guardian’ database via fusion centers, which ultimately connect to the FBI, the DHS and even the Department of Defense,” Watson continues. Guardian replaced the TALON database. It was created on orders issued by the deputy defense secretary during the Bush regime, the neocon Paul Wolfowitz, and was criticized for gathering information on antiwar activists and other political activists who posed no credible threat to the empire. TALON reports were collected by Defense Department agencies including law enforcement, intelligence, counterintelligence and security, and were analyzed by a secretive Pentagon agency, the Counterintelligence Field Activity. CIFA was supposedly “disestablished” and the TALON database shut down. Of course, that was merely public relations spin – intelligence databases are never shut down. Instead, they are repurposed. TALON is now Guardian and it continues its legacy of collating data on threats to the establishment and its profitable occupations and covert wars in Pakistan, Yemen, and elsewhere. Guardian has nothing to do with al-Qaeda, the fake terror group that takes its name from another database. The Post Office data collection scheme will undoubtedly be used in the same way Google’s StreetView was used – to vacuum up wireless data and ferret out intelligence. In July, Consumer Watchdog issued a newswire calling for the Energy and Commerce Committee to conduct hearings into privacy violations by Google. John M. Simpson of the non-profit group said “it appears that Google holds classified U.S. government contracts to supply search and geospatial information to the U.S. government.”
Now the Post Office is about to be thrown into the effort to create a massive and all-encompassing electronic panopticon. “Such a system could aid in homeland security by rapidly detecting chemical agents, radiological materials and, eventually, biological attacks,” Ravnitzky avers. It will also be used to determine user behavior over public Wi-Fi hotspots, a charge made against Google by the German Data Protection Authority in May. The government is not worried about al-CIA-duh or the remote possibility of a biological attack. It is concerned – as the DHS report on “rightwing extremism” and the similar report issued by MIAC revealed – about the political activity of ordinary Americans. “Neither snow nor rain nor heat nor gloom of night stays these couriers from the swift completion of their appointed rounds,” is said to be the motto of the Post Office. If the government has its way, the motto will need to be updated to include “and data-mine your personal information” to make sure you are not a threat to the establishment.
NSA? The Postal Service
by Courtney Clark | People's Blog for the Constitution | June 23, 2014 With the ongoing debate about mass spying by the NSA, many Americans are reconsidering their reliance on telephone and electronic communications. But is it safe to trust the US Postal Service (USPS)? You may not want to know…. In 2013, the Postal Inspection Service processed tens of thousands of mail covers, and also “photograph[ed] the exterior of every piece of paper mail” processed by the USPS through the Mail Isolation Control and Tracking program revealed last year. Last July, the New York Times explained that “Snail mail is subject to the same kind of scrutiny that the National Security Agency has given to telephone calls and e-mail.” A Postal Service Inspector General report released last month suggests that even the more restrained mail cover program should raise concerns. A mail cover is used to record data presented on the outside of a piece of mail. This service is used for investigative measures within the Postal Inspection Service, but is also available to law enforcement and intelligence agencies. According to the USPS Inspector General, law enforcement agencies requesting mail covers must first meet the requirements of the US Postal Inspection Service. They must demonstrate clear reasoning justifying their need to use these services, including details on the violation of law, or proof that a crime has been committed and how the mail cover would be of assistance in the investigation. The Inspector General’s recent audit covered September 2013 through May 2014, and shows that post office officials failed to put in place compliance procedures over the course of 3 years, placing both privacy and security at risk. The audit reveals that post office personnel were not abiding by Postal Service requirements when handling mail covers. Based on 196 randomly analyzed criminal mail cover requests, 21% were approved by someone not in an authoritative position; and 13% did not have accurate or required justification. Another 27% of mail covers received from the Criminal Investigative Service Center (CISC) for processing were not entered into the Inspection Service Integrated Information System (ISIIS) within the allotted time period for compliance and regulation checks. This means that a whopping 61% of all criminal mail covers across the nation had some sort of legal deficiency. Also, ISIIS has produced questionable and unreliable information due to insufficient system controls. Due to this deficiency in the ISIIS, 928 mail covers were found to remain active even though they should have ended many moons ago. These findings led the Inspector General to articulate a disturbing concern:
The public is most definitely concerned with dragnet invasions of privacy. Just a month after the Snowden disclosures forced a long overdue (and still ongoing) debate about government surveillance, the press also revealed the USPS Tracking Program, which stores metadata about snail mail for up to 6 years. Leslie James Pickering, one of many investigative targets, accidentally received a handwritten card delivered to his home in September of 2012 with instructions to monitor and copy every letter and package sent there. Shocked by this apparent “confidential” note, Post Office personnel soon confirmed they were keeping track of all mail addressed to Mr. Pickering, but did not care to share anything else. His participation in the Earth Liberation Front, an environmental group described by the FBI as “eco-terrorists,” might explain the basis for the government interest. Group affiliation, however, is constitutionally protected under the First Amendment, so even that basis for scrutiny would not suffice to render USPS surveillance legal. The USPS Tracking program was created after the anthrax attacks in 2001. Mark D. Rasch, who worked on numerous fraud cases using mail covers at the Department of Justice, said, “In the past, mail covers were used when you had a reason to suspect someone of a crime…now it seems to be, ‘Let’s record everyone’s mailso in the future we might go back and see who you were communicating with.’ Essentially you’ve added mail covers on millions of Americans.”
Germans under Hitler denounced their neighbors and friends not because they genuinely believed them to be a security threat, but because they expected to selfishly benefit from doing so, both financially, socially and psychologically via a pavlovian need to be rewarded by their masters for their obedience.
At the height of its influence around one in seven of the East German population was an informant for the Stasi. As in Nazi Germany, the creation of an informant system was wholly centered around identifying political dissidents and those with grievances against the state, and had little or nothing to do with genuine security concerns.
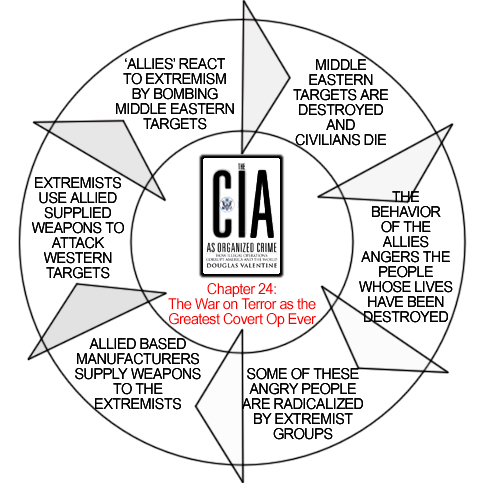
SOME BACKGROUND War on Terror: Greatest Covert Op http://www.consortiumnews.com/2010/083110b.html
LINKS:
Torture Pre Conditioning
Since 9/11, the globalist puppets have been dancing about their little stage conducting their rhetoric on torture. This rhetoric is tied to the Hegelian Dialectic. A mass mind control device with the sole purpose to precondition the public. A fantasy, where we all believe our leaders are firmly in charge of what is right and just. Flip the script on that notion and the CIA's playbook reveals itself, A giant mind game presented to the average American superimposed on a massive infrastructure determined to cross the finish line on the END GAME. http://www.infowars.com/cuba-hip-hop-...
Mastering The Human Domain
A closer look at the upcoming Jade Helm military exercise, specifically its “master the human domain” motto, reveals a larger agenda in regards to domestic policy. ...“They’re building an infrastructure of tyranny,” stated Infowars David Knight. “There’s a legal infrastructure with things like the NDAA, there’s a technical infrastructure with things like the capability to do dragnet surveillance, and then of course there is going to be a military and law enforcement infrastructure, and those are merging.”
Synopsis
Full Presentation
LINK: TOTAL POPULATION CONTROL
A woman's look at the Contact Tracer documents. This is BAD news. "Isolation" and "quarantine" can be imposed again and again, the way the documents read.
As the people of the world grapple with a pandemic that is demonstrably less deadly than originally reported, the public is being primed to accept an exponential increase in invasions of personal liberty and privacy. Every day the public grows more weary of lock downs which seem to never end, and the bankrupting of individuals and businesses around the world. Amidst the frustration and protest a solution is being presented. To return to normal, we are told, we must accept certain changes to how our world operates. Of course, this is actually a push to a “new normal” which will mark the world after COVID-19. Just like the attacks of September 11, 2001, there is the world we knew before, and there is the post-9/11 era. We are currently in the middle of the COVID-19 era and a shift to post-COVID19 life will not happen without the completion of local, state, national, and international programs which identify potential infectees, test them, and, if positive, quarantine them in their homes or other government facilities. This is what is known as a contact tracing program. You have likely heard the term in recent days and weeks because a number of local and state bodies within the United States are considering or already launching contact tracing programs. Nations like China, Singapore, India, South Korea, and Israel have implemented these programs but have also faced criticism from digital rights advocates for violations of privacy protections. So what exactly is contact tracing?Contact tracing is a process of identifying individuals who may have come into contact with an infected person, collecting information about their contacts, and then tracing the contacts of infected individuals. All persons who may have come into contact with an infected individual are tested for infection, treated for the infection, and their contacts traced as well. Regarding the COVID-19 pandemic, we are seeing calls for digital contact tracing using cell phones to notify individuals when they may have come into contact with an infected person or visited a hot spot of infection. Digital contact tracing apps use Bluetooth to track encounters, a move which is supposed to anonymize actual location data. Other forms of contact tracing apps involve the use of location data gathered from cellular networks. Additionally, tech giants Apple and Google have promised to help slow the spread of the virus with new tracking apps that the public can download to report themselves as infected. Using Bluetooth, the phones will warn app users when they are near an infected person or a hot spot. The programs will use data from Android and iPhone users who volunteer for the program later this month. Jennifer Granick, a surveillance and cybersecurity attorney with the American Civil Liberties Union told Politico that the joint effort between the tech companies “appears to mitigate the worst privacy and centralization risks.” However, “there is still room for improvement.” Microsoft is collaborating with the University of Washington on their own project which the university promotes as a privacy based contact tracing app. Researchers with the University of Washington and UW Medicine worked with volunteers from Microsoft to develop CovidSafe. The researchers stated that the app will alert users about potential exposure to COVID-19, but will do so without giving up anyone’s privacy. “With CovidSafe, all information is stored locally on your phone unless you choose to share that you’ve tested positive,” explained Justin Chan, a UW doctoral student in the Paul G. Allen School of Computer Science & Engineering. “Only then is your data sent to a secure server, and the app alerts anyone who has been nearby. After these notifications are sent, all the information is deleted.” CovidSafe is not the only attempt to build a privacy-based contact tracing program. In April, a team of researchers launched Coalition, a free contact tracing app designed to protect users’ privacy and protect communities during the COVID-19 crisis. Coalition claims to utilize secure Bluetooth Low Energy (BLE) and cryptography to protect a user’s identity by generating random anonymous IDs. The app uses Coalition’s Whisper Tracing, an open source privacy-first protocol that randomizes a user’s device identity and does not share identifiable information with the cloud. Building a Contact Tracing Army
New York Governor Andrew Cuomo recently announced efforts by NY state to hire thousands of contact tracers. The state’s contact tracing program is being developed with $10 million from former New York City Mayor Michael Bloomberg and support from Johns Hopkins University. Cuomo stated that applicants will need to go through a training program and pass an online exam before being granted the authority of contact tracer. The state’s program will involve identifying COVID-19 positive individuals, interviewing them about contacts in the previous two weeks, and then those contacts must isolate for two weeks. By late April, calls for contact tracing had grown so loud that Congressman John Garamendi introduced a bill that would “expand volunteer opportunities within AmeriCorps and the Federal Emergency Management Agency”. Garamendi is the Co-Chair of the AmeriCorps, a nationwide volunteer force created by former President Bill Clinton in 1993. The Orwellian bill – “Undertaking National Initiatives to Tackle Epidemic Act” or the UNITE Act – would allow AmeriCorps and FEMA to create a national contact-tracing corps. “The coronavirus pandemic has put an unprecedented strain on our society, and our
nation requires a significant scaling of testing and contact tracing in order to flatten the curve and lift
stay-at-home orders,”
Garamendi stated. Coincidentally, the UNITE Act lines up with recent calls for a contact tracing “army”. The South Carolina Department of Health and Environmental Control called for more contact tracers in the state. Dr. Joan Duwve, the Director of Public Health for DHEC, said being able to test someone rapidly was necessary. “We need an army of contact tracers to respond in a short time to someone who has a positive diagnosis,” Duwve said. On the opposite side of the country, California Governor Gavin Newsom has partnered with the University of California, Los Angeles and the University of California, San Francisco to train more than 3,000 employees to become “coronavirus detectives“. During a live streamed press conference Newsom described the efforts as a training academy designed to build an “army” of 20,000 people who can test, trace, and isolate people who may be infected. Sonia Angell, California Department of Public Health director and State Health Officer, also stated that the new contact tracing program will be connected to California’s existing digital disease surveillance platform. Angell claims the database will be confidential. The push for international contact tracing programs has also blossomed in nations like South Korea and China, who are praised for their aggressive approaches to slowing the growth of the virus. Forbes noted that South Korea has had a massive drop in COVID-19 diagnoses largely due to “mass rapid testing and comprehensive digitally-enabled contact tracing”. South Korea has also used GPS phone tracking, CCTV cameras, credit card transaction monitoring, and automated text alerts as part of a comprehensive universal contact tracing program. The Chinese government approach is what you would expect from a totalitarian communist state: an all encompassing app that pretty much “controls your life.” Bloomberg describes China’s contact tracing app as a “public-private ‘health code’ system” which issues one of three risk assessments in the form of a colored QR code. “A green QR code, which denotes a low risk of having the virus, is the general default, while coming into contact with an infected person can trigger a yellow code and a mandatory quarantine. Red is for a likely or confirmed case,” Bloomberg reported. It does not take an extremely paranoid mind to see how this system could be easily abused. The Indian government recently launched their contact tracing app – Aarogya Setu – which quickly became the fastest downloaded app on record, with more than 83 million users. Although India is not the first nation to implement a nationwide contact tracing program, the nation lacks strong privacy and data protection laws for its more than 1.3 billion citizens. The Guardian reported that the pandemic is being “used as a pretext to erode privacy and freedom of speech in the name of ‘winning the war’ against coronavirus.” In April The Guardian revealed that a draft government memo explained how the data gathered by the contact-tracing app could be “de-anonymized” by government officials. Israel’s attempted grab for tyrannical health surveillance powers were recently hampered by a decision from the Supreme Court which banned the intelligence community from tracing the phone location of those infected with COVID-19. The Israeli Shin Bet service was given emergency powers through the end of April before the court warned of a “slippery slope” where the surveillance tool could be used against innocent individuals. Whitney Webb recently reported that at least three tech companies involved in the build out of the “coronavirus surveillance system” have connections to Israel’s government and the usual Big Tech players. Following The Orders of the WHO
In early April, Dr. Michael Ryan, the head of the World Health Organization’s team responsible for the international containment and treatment of COVID-19, called for looking into families to find potentially sick individuals and isolate them from their families. “Due to lock down, most of the transmission that is actually happening in many countries now is happening in the household at a family level,” Ryan stated. “In some senses, the transmission has actually been taken off the streets and pushed back into family units… Now we need to go and look into families, and find those people who are sick and remove them and isolate them in a safe and dignified manner.” Ryan was also involved in the now-infamous Event 201, a global pandemic simulation, conducted on October 18, 2019, funded by the Bill and Melinda Gates Foundation, the World Economic Forum, and John Hopkins University Center for Health Security. Ryan’s bio states that “from November 2013 to October 2014 he worked with GPEI as Middle East Polio Response Coordinator” and partnered with the Bill and Melinda Gates Foundation (among others) for a vaccination program which reached 25 million children in eight target countries as part of 44 mass polio vaccination campaigns. Ironically enough, the WHO released a document in 2019 which states that under no circumstances should contract tracing be used. The document, first reported on by independent researcher Kenny Palurintano, details the WHO’s views on Non-pharmaceutical intervention (NPI) in response to a pandemic. In section 6.1, “Contact Tracing,” under “quality of evidence”, it states, “There is a very low overall quality of evidence that contact tracing has an unknown effect on the transmission of influenza.” Additionally, under the “Executive Summary”, in Table 1, the WHO lists contact tracing under the heading “Not Recommend In Any Circumstances”. Despite the WHO’s own documents denying the validity of contact tracing, officials in Ventura County are heeding the call of WHO official Dr. Michael Ryan. At a May 4 press conference, Ventura County Public Health Director Dr. Robert Levin said those who live in homes where they could expose family members to COVID-19 could be removed from their homes and moved into other health facilities. “We also realize that as we find more contacts, some of the people we find are going to have trouble being isolated. For instance, if they live in a home where there is only one bathroom and there are three or four other people living there, and those people don’t have COVID infection, we’re not going to be able to keep the person in that home,” Levin stated. “Every person who we’re isolating, for instance, needs to have their own bathroom. And so we’ll be moving people like this into other kinds of housing that we have available.” The Ventura County Public Health board did not elaborate on what other kinds of housing might be made available to those unable to quarantine at home. If there is a silver lining to the growing support for contact tracing, it might be the public’s own hesitance to join. According to Forbes, nation-states need about 60 percent of their population to adopt and regularly use the tool for it to be effective. Forbes reports that most cities are not likely to achieve 60% or even 40% compliance. Unfortunately, Forbes reminds us, “It’s a relentless fight. And it takes an army of tracers.” Forbes also notes that cities will need to “force changes of behavior” before reopening society. “Contact-tracing apps are being seen as one of the conditions of ending lockdowns—mandating and enforcing their use might become a logical next step.“ How exactly the cities, states, and nations will enforce the use of contact tracing apps remains to be seen, but we are already seeing a rise in reports of arrests of individuals who violate orders to close businesses, stay home, and practice social distancing. What should we expect to see when an individual or an entire community chooses to opt-out of contact tracing surveillance programs? It is important to understand that contract tracing is only one part of an overall strategy which poses a danger to liberty and privacy. In addition to creating mobile apps which snitch on you, Apple, Facebook and Google are also sharing data with the government to help determine if the public is following social distancing guidelines. MIT Technology Review reported that at least one company is selling an app that uses machine learning Artificial Intelligence to monitor social distancing. Meanwhile, Reuters reported that Amazon is using similar software to enforce social distancing between their warehouse staff. There are also reports of “pandemic drones” flying above the skies of Connecticut and Maryland to monitor social distancing and take temperatures. Together these technologies represent the foundation of the Technocratic State, built on top of the fears of a public which has been conditioned to accept any and all relief from the terrifying round-the-clock coverage of the COVID-19 pandemic. If the public accepts the COVID1984 Technocracy in the name of “getting back to normal” it’s likely the world we have known will be regarded as a relic of a past era, a quaint idea of what life was like and what it could be, if only the public could defeat the new invisible enemy, COVID19. However, it’s important to understand the institutions which are benefitting from the current pandemic. Only by acknowledging the true power players – those who maneuver behind the scenes to profit and enslave – can the free hearts and minds of the world defeat the true enemy: COVID-1984.
In the video below, Alex Jones highlights how the Guardian Centers video is yet another startling indication that authorities in the United States are preparing for civil unrest as America increasingly begins to resemble a militarized police state.
U.S. Army Training to Fight Black Americans
LINKS: Posse Comitatus Act , Posse Comitatus2 , REX 84 , Fema Camps , Fema Camps 2 , Re-education Camps
Government Recruiting Spies for Fire Department
Postal Service Caught Deploying Face-Scanning
Cameras
by Mikael Thalen | Infowars.com | March 12, 2015 A face and license plate scanning camera was torn from the ground outside a Colorado post office this week less than one hour after being discovered by local reporters.
The camera, run by the United State Postal Inspection Service, the postal service’s law enforcement unit, was hidden inside a utilities box near the exit of the Golden Post Office. According to FOX31 Denver investigative reporter Chris Halsne, the camera was mysteriously removed almost immediately after he began asking unit representatives why the device was capturing local residents. The U.S. Postal Service responded by denying that “random surveillance” was being conducted despite the camera appearing to capture every driver that left the property. “(We) do not engage in routine or random surveillance. Cameras are deployed for law enforcement or security purposes, which may include the security of our facilities, the safety of our customers and employees, or for criminal investigations,” U.S. Postal Inspector Pamela Durkee said. “Employees of the Postal Inspection Service are sworn to uphold the United States Constitution, including protecting the privacy of the American public.” Employees of the post office, who were allegedly unaware of the camera, told Halsne that the surveillance device was not linked into their normal security system. Investigating the matter further, FOX31 was unable to locate any “criminal search warrants on file in city, county, or federal court” that related to the post office’s surveillance. “FOX31 Denver filed multiple Freedom of Information Act requests with the Postal Service, Postal Inspection Service, and Office of the Inspector General in an attempt to identify the cost and scope of the Postal Inspection Service surveillance program,” the article states. “None of the agencies could provide a written data retention policy, which would detail how long USPIS could keep the images agents have been collecting from the Golden post office camera and other cameras around the Denver area.” Hop-On Incorporated, a company known to sell surveillance systems to the U.S. Postal Service, also refused to disclose information on whether they provided cameras for Colorado’s program. “Our FOIA requests for federal contracts and financial information about Hop-On and other contractors who sell USPS and USPIS camera equipment were returned to us void of all information,” the article says. The incident suggests that the camera was removed by the postal service in an attempt to hide the program’s details, unsurprising given the U.S. Postal Service’s long history of surveillance. A 2013 article in the New York Times detailed the postal service’s Mail Isolation Control and Tracking program, which records the metadata of millions of pieces of mail. “In the past, mail covers were used when you had a reason to suspect someone of a crime,” said Mark D. Rasch, a Justice Department employee said. “Now it seems to be, ‘Let’s record everyone’s mail so in the future we might go back and see who you were communicating with.’ Essentially you’ve added mail covers on millions of Americans.” Colorado’s surveillance program highlights how nearly every activity of the American public is under constant surveillance regardless of criminal activity. Facebook @ https://www.facebook.com/mt.examiner
Big Brother - InfraGard -
Surveillance on U.S. citizens http://www.facebook.com/ConspiracyThe...
http://www.infragardmembers.org/
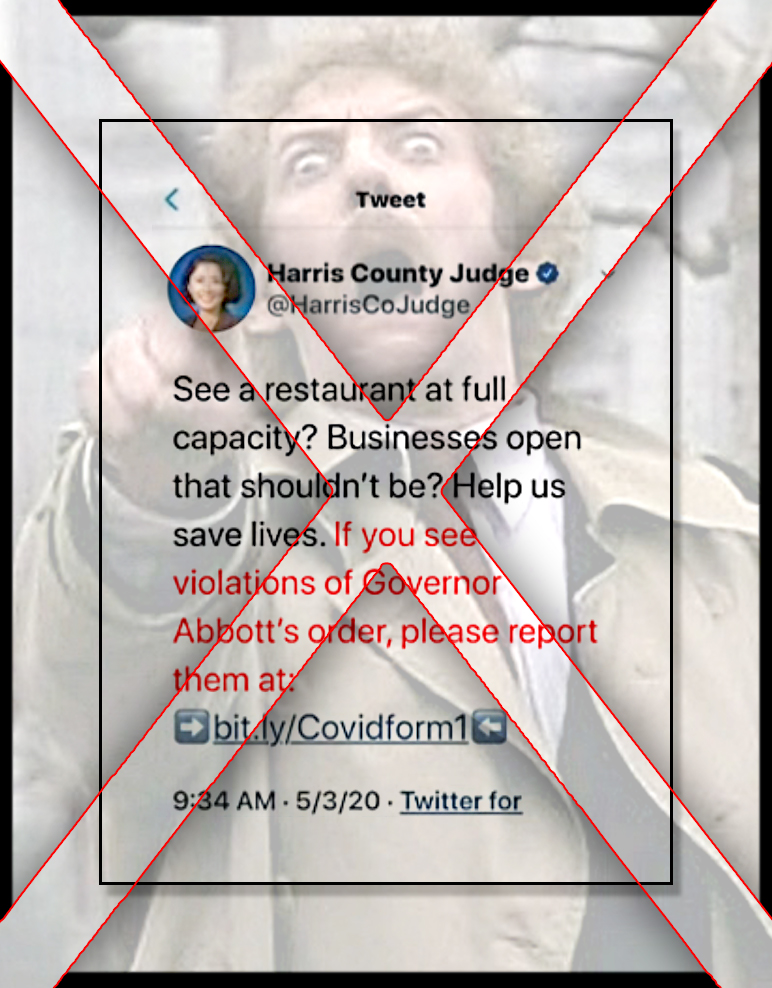
FBI: Paying Cash For a Cup of Coffee a ‘Potential Indicator of Terrorist Activity’ Advisory aimed at Internet Cafe owners characterizes mundane behavior as “suspicious activity” Paul Joseph Watson An FBI advisory aimed at Internet Cafe owners instructs businesses to report people who regularly use cash to pay for their coffee as potential terrorists. The flyer, issued under the FBI’s Communities Against Terrorism (CAT) program, lists examples of “suspicious activity” and then encourages businesses to gather information about individuals and report them to the authorities. “Each flyer is designed for a particular kind of business,” writes Linda Lewis, a former policy analyst and planner for the U.S. government. “For example, this list was prepared for owners of internet cafes. Unquestionably, someone planning a terrorist attack has engaged in one or more of the “suspicious” activities on that list. But so, too, have most of the estimated 289 million computer users in this country.” Indeed, the flyer aimed at Internet Cafe owners characterizes customers who “always pay cash” as potential terrorists. Of course, the vast majority of people who visit Internet Cafes use cash to pay their bill. Who uses a credit card to buy a $2 dollar cup of coffee? A lot of smaller establishments don’t even accept credit cards for amounts less than $10 dollars. Other examples of suspicious behavior include using a “residential based Internet provider” such as AOL or Comcast, the use of “anonymizers, portals, or other means to shield IP address” (these are routinely used by mobile web users to bypass public Internet filters), “Suspicious communications using VOIP,” and “Preoccupation with press coverage of terrorist attack” (this would apply to the vast majority of people who work in the news or political blogging industry). Searching for information about “police” or “government” is also listed as a potential indication of terrorism, as is using a computer to “obtain photos, maps or diagrams of transportation, sporting venues, or populated locations,” which would apply to virtually anyone who uses Google Maps or Google Earth. People who may wish to keep private the contents of a personal email or an online credit card purchase by attempting to”shield the screen from view of others” are also characterized as potential terrorists. Business owners who spot patrons engaging in these types of activities are encouraged to call the FBI’s Joint Regional Intelligence Center (JRIC), after first gathering information on license plates, names, ethnicity, and languages spoken. In total, there are 25 different CAT flyers aimed at businesses from across the spectrum – everything from hobby shops to tattoo parlors. As we have documented on numerous occasions, the federal government routinely characterizes mundane behavior as extremist activity or a potential indicator of terrorist intent. As part of its ‘See Something, Say Something’ campaign, the Department of Homeland Security educates the public that generic activities performed by millions of people every day, including using a video camera, talking to police officers, wearing hoodies, driving vans, writing on a piece of paper, and using a cell phone recording application,” are potential signs of terrorist activity. The CAT program again underscores how federal authorities are empowering poorly trained citizens to become terrorist hunters, stoking fears that America is sinking deeper into a Stasi-style informant society. Last week we reported on how the DHS had trained hot dog sellers and other vendors to spot terrorists at this past weekend’s Super Bowl event.
LINKS: THE FAKE WAR ON TERROR , F.B.I.
EVERYONE IS A
TERRORIST First published at 07:26 UTC on August 6th, 2019. SHOW NOTES: https://www.corbettreport.com/?p=32302 The term "conspiracy theory" was weaponized by the CIA half a century ago. At first it was merely
used to marginalize those who question government narratives. But now that weapon is being loaded and pointed at
our heads. Can a "conspiracy theorist" false flag be far behind? James examines the new FBI document on conspiracy
theorists LINKS: Propaganda History | F.B.I.
LINK: Subverting The Public
LINK: THE FAKE WAR ON TERROR
EVERYONE
How could there be a War on Terror and actually say that we're having a war against terrorism, and leave the borders wide open? If you were the President of the United States, or I were the President of the United States, and 9/11 really happened the way they want us to believe it happened, the first thing you would do is shut down the borders, so people couldn't get in the country to harm you. But they left the borders wide open. Because the bankers want the borders open, because they want a one-world government. They want a North American Union. They don't want borders here. 9/11 was only a manifestation. It was done to create a fear in the American public, so that we will obey what they want us to do.
THE FAKE WAR ON TERROR , INFAMOUS 9/11 , False Flag Event , ISIS/ALQAEDA , America Armed ISIS!! , Naked Body Scanners , American Border Debacle , Feds Radiating Americans , Illegal Checkpoints In America , Mobile Van Radiating the Public , Police Trained That Informed Americans Are Terrorists , The NSA (National Security Agency) , The Federal Reserve , Fusion Centers , TSA , N.W.O.

LINK: American Border
Debacle
It’s no longer Al-Qaeda, it’s now supposedly your friends and neighbors. This is the prevailing meme of every tyrannical fascist regime in history.
Attorney General Holder: American People Are Terrorists
THE WAR ON TERROR IS AN ABSOLUTE FRAUD
[OBAMA RELEASES MAJOR TERRORIST ORGANIZERS OF THE TALIBAN] Could Obama Face Impeachment For Bergdahl release
What happened in the last few weeks to change the Bergdahal situation? Was he a CIA operative, or was this a failed attempt to take the heat off the VA scandal? Impeachment now very valid argument Jay Carney 2013: we won't transfer detainess without consulting congress Obama clearly broke the law Is this a ramp up to "White al Qaeda"
LINK: THE FAKE WAR ON TERROR!
Alex Jones breaks down the bigger picture behind the move to turn the war on terror against American citizens EVERYONE IS A
TERRORIST White House Tells Parents: Children Could Be Terrorists!
I have told you this was coming. Under the new homeland we are all the enemy in the eyes of the occupiers. LINKS: You Are Being Targeted , Assassination Program , [ AL-QAEDA EXPOSED!! ] , Terrorism Big Dirty Secret , AGENDA 21 Cliven Bundy Case Example , Police Trained That Informed Americans Are Terrorists , Troops Ordered To Kill All Americans Who Do Not Turn In Guns , Posse Comitatus Act , Posse Comitatus2 , Police State 1 , Police State 2 , Police State 3 , Police State 4 , The Fake War On Terror
THE GLOBALISTS MOVE FROM THEIR ALQAEDA CREATION, TO FABRICATING HOMEGROWN DOMESTIC TERROR
Several years ago, after his popular video “Mad As Hell” was released and Aaron Russo began his campaign to become Governor of Nevada, Russo was noticed by Nicholas Rockefeller and introduced to him by a female attorney. Seeing Russo’s passion and ability to affect change, Rockefeller set about on a subtle mission to recruit Russo into the elite’s CFR. Watch the full interview here: Reflections and Warnings.
Aaron Russo talks about the CFR...And The Fake War On Terror!
Aaron Russo talks about the CFR...And The Fake War On Terrorism!
LINKS: Reflections and Warnings , Road to World Government , CASHLESS TRACKABLE SOCIETY , Educational System Dismantlement , The Fake War On Terror , 911 The Road to Tyranny , INFAMOUS 9/11 , N.W.O. , C.F.R.
***BACKGROUND REFERENCE*** Technocracy is a replacement economic system for Capitalism and Free Enterprise, and is represented by the United Nations’ program for Sustainable Development and “Green Economy.” It proposes that all means of production and consumption would be controlled by an elite group of scientists and engineers (technocrats) for the good of mankind. Technocracy was originally architected in the 1930s but regained favor when adopted by the Trilateral Commission in 1973, under their “New International Economic Order” program. https://www.technocracy.news/faq-2/
The Roots of Technocracy with Expert Patrick M. Wood Alex welcomes to the broadcast The August Forecast & Review Editor Patrick M. Wood to discuss
how the global elite within the Trilateral Commission are replacing capitalism with their own technocracy in
order to create a New International Economic Order.
TOTAL SURVEILLANCE SOCIETY
GO HERE TO UNDERSTAND HOW ALL THIS FITS WITHIN
LEARN HOW THE REAL POLITICAL SYSTEM WORKS
HERE: TRAGEDY & HOPE
101
Is "democracy" just a carefully managed con game? Professor Quigley not only spent decades researching and writing about those who secretly control the machinery of our “representative governments,” he was permitted to examine their secret papers. He was invited in, but he ultimately betrayed their trust when he exposed their plans and their methods. - Joe Plummer -
G. Edward Griffin The Quigley Formula Jason Bermas G. Edward Griffin The Quigley Formula Bill Clinton And More From The Archives! Another great speaker who lays out a compelling narrative of history in the archived series! https://www.gofundme.com/f/bermasbrig... Bitcoin - 1HHdgXD5e1DJrDqbEGWbnvzj2eb739eVVo | #BermasBrigade #BritishRoyalty
#ThePredatorClass
REACH OUT TO OTHERS [Help Educate Family And Friends With This Page And The Links Below]
MORE: The Balkanization of America | Snitch Phone Application | Tattle-Tale Articles | YouTube Tattling | Tattle-Tale Squads and Surveillance | Post Office Trucks Stasi Data Collection Nodes | Big Brother/Sis & Surveillance Systems | The NSA (National Security Agency) | [ AL-QAEDA EXPOSED!! ] | C.I.A. | F.B.I.Propaganda History | Propagandizing Through Games | Bread and Circus | Learned Helplessness | Educational System Dismantlement | Media Controllers | Media Controllers2 | Media Controllers3 | FALSE LEFT/RIGHT PARADIGM | Subverting The Public
| ||||||||||||||||||||||||||||||||||||||||||