welcome
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
The NSA
The National Security Agency (NSA) is a cryptologicintelligence agency of the United States Department of Defense responsible for the collection and analysis of foreign communications and foreign signals intelligence, as well as protecting U.S. government communications and information systems,[1] which involves information security and cryptanalysis/cryptography. The NSA is directed by at least a lieutenant general or vice admiral. NSA is a key component of the U.S. Intelligence Community, which is headed by the Director of National Intelligence. The Central Security Service is a co-located agency created to coordinate intelligence activities and co-operation between NSA and other U.S. military cryptanalysis agencies. The Director of the National Security Agency serves as the Commander of the United States Cyber Command and Chief of the Central Security Service.[2] By law, NSA's intelligence gathering is [SUPPOSEDLY] limited to foreign communications, although domestic incidents such as the NSA warrantless surveillance controversy have occurred.
“Domestically, they’re pulling together all
the data about virtually every U.S. citizen in the country and assembling that information, building communities
that you have relationships with, and knowledge about you; what your activities are; what you’re doing. So the
government is accumulating that kind of information about every individual person and it’s a very dangerous
process.”
Former NSA Head Exposes Agency's True Crimes
Published on Apr 30, 2015 William Binney, a legendary NSA mathematician developed the revolutionary logic and architecture that is now used to spy on everybody in the world. When the NSA decided to use his programs on US citizens he became one of the biggest whistleblowers in the history of the NSA. He started the debate and the avalanche of understanding in regards to illegal surveillance, and is revealing inside knowledge on some of the biggest government secrets to date. Related: NSA WHISTLEBLOWER: ‘WE’RE NO LONGER A COUNTRY WITH A GOVERNMENT, WE’RE A GOVERNMENT WITH A COUNTRY’ - http://www.infowars.com/nsa-whistlebl...
Ex-NSA Analysts on Their Top-Secret Discoveries Two former National Security Agency analysts talk about when they discovered the agency
was
'NSA owns entire network anywhere in the world' - Whistleblower William Binney - Published on Jul 4, 2014 NSA global reach is omnipresent. The US intelligence controls the entire cyber network across the globe, violating individual piracy by storing endless data on its increasingly enlarged servers, former NSA crypto-mathematician, William Binney, told RT. READ FULL SCRIPT http://on.rt.com/y1q1fy
The Ultimate Goal Of The NSA Is Total Population Control At least 80% of all audio calls, not just metadata, are
recorded and stored in the US, says whistleblower William Binney
William Binney is one of the highest-level whistleblowers to ever emerge from the NSA. He was a leading code-breaker against the Soviet Union during the Cold War but resigned soon after September 11, disgusted by Washington’s move towards mass surveillance.
“At least 80% of fibre-optic cables globally go via the US”, Binney said. “This is no accident and allows the US to view all communication coming in. At least 80% of all audio calls, not just metadata, are recorded and stored in the US. The NSA lies about what it stores.” The NSA will soon be able to collect 966 exabytes a year, the total of internet traffic annually. Former Google head Eric Schmidt once argued that the entire amount of knowledge from the beginning of humankind until 2003 amount to only five exabytes. Binney, who featured in a 2012 short film by Oscar-nominated US film-maker Laura Poitras, described a future where surveillance is ubiquitous and government intrusion unlimited. “The ultimate goal of the NSA is total population control”, Binney said, “but I’m a little optimistic with some recent Supreme Court decisions, such as law enforcement mostly now needing a warrant before searching a smartphone.” He praised the revelations and bravery of former NSA contractor Edward Snowden and told me that he had indirect contact with a number of other NSA employees who felt disgusted with the agency’s work. They’re keen to speak out but fear retribution and exile, not unlike Snowden himself, who is likely to remain there for some time. Unlike Snowden, Binney didn’t take any documents with him when he left the NSA. He now says that hard evidence of illegal spying would have been invaluable. The latest Snowden leaks, featured in the Washington Post, detail private conversations of average Americans with no connection to extremism. It shows that the NSA is not just pursuing terrorism, as it claims, but ordinary citizens going about their daily communications. “The NSA is mass-collecting on everyone”, Binney said, “and it’s said to be about terrorism but inside the US it has stopped zero attacks.” The lack of official oversight is one of Binney’s key concerns, particularly of the secret Foreign Intelligence Surveillance Court (Fisa), which is held out by NSA defenders as a sign of the surveillance scheme's constitutionality. “The Fisa court has only the government’s point of view”, he argued. “There are no other views for the judges to consider. There have been at least 15-20 trillion constitutional violations for US domestic audiences and you can double that globally.”
Binney recently told the German NSA inquiry committee that his former employer had a “totalitarian mentality” that was the "greatest threat" to US society since that country’s US Civil War in the 19th century. Despite this remarkable power, Binney still mocked the NSA’s failures, including missing this year’s Russian intervention in Ukraine and the Islamic State’s take-over of Iraq. The era of mass surveillance has gone from the fringes of public debate to the mainstream, where it belongs. The Pew Research Centre released a report this month, Digital Life in 2025, that predicted worsening state control and censorship, reduced public trust, and increased commercialisation of every aspect of web culture. It’s not just internet experts warning about the internet’s colonisation by state and corporate power. One of Europe’s leading web creators, Lena Thiele, presented her stunning series Netwars in London on the threat of cyber warfare. She showed how easy it is for governments and corporations to capture our personal information without us even realising. Thiele said that the US budget for cyber security was US$67 billion in 2013 and will double by 2016. Much of this money is wasted and doesn't protect online infrastructure. This fact doesn’t worry the multinationals making a killing from the gross exaggeration of fear that permeates the public domain. Wikileaks understands this reality better than most. Founder Julian Assange and investigative editor Sarah Harrison both remain in legal limbo. I spent time with Assange in his current home at the Ecuadorian embassy in London last week, where he continues to work, release leaks, and fight various legal battles. He hopes to resolve his predicament soon. At the Centre for Investigative Journalism conference, Harrison stressed the importance of journalists who work with technologists to best report the NSA stories. “It’s no accident”, she said, “that some of the best stories on the NSA are in Germany, where there’s technical assistance from people like Jacob Appelbaum.” A core Wikileaks belief, she stressed, is releasing all documents in their entirety, something the group criticised the news site The Intercept for not doing on a recent story. “The full archive should always be published”, Harrison said. With 8m documents on its website after years of leaking, the importance of publishing and maintaining source documents for the media, general public and court cases can’t be under-estimated. “I see Wikileaks as a library”, Assange said. “We’re the librarians who can’t say no.” With evidence that there could be a second NSA leaker, the time for more aggressive reporting is now. As Binney said: “I call people who are covering up NSA crimes traitors”.
NSA Edward
Snowden: 'I don't want to live in
NSA - KNOWING ALL ABOUT US
Nightly News: Obama's NSA Close to Knowing All About Us
***BACKGROUND REFERENCE*** Technocracy is a replacement economic system for Capitalism and Free Enterprise, and is represented by the United Nations’ program for Sustainable Development and “Green Economy.” It proposes that all means of production and consumption would be controlled by an elite group of scientists and engineers (technocrats) for the good of mankind. Technocracy was originally architected in the 1930s but regained favor when adopted by the Trilateral Commission in 1973, under their “New International Economic Order” program. https://www.technocracy.news/faq-2/
The Roots of Technocracy with Expert Patrick M. Wood Alex welcomes to the broadcast The August Forecast & Review Editor Patrick M. Wood to discuss
how the global elite within the Trilateral Commission are replacing capitalism with their own technocracy in
order to create a MORE:
Israel Hacking the World Know More News Know More News with Adam Green Support Know More News! Follow me on Social Media:
Know More News Know More News with Adam Green
Israel's Tech
Know More News Premiered May 22, 2019 Know More News with Adam Green https://www.KnowMoreNews.org/ Support Know More News! Paypal Donations - https://www.paypal.me/KnowMoreNews Patreon - https://www.patreon.com/AdamGreen Venmo - @Know-More-News Know More News Know More News with Adam Green Support Know More News! Paypal Donations - https://www.paypal.me/KnowMoreNews Patreon - https://www.patreon.com/AdamGreen Venmo - @Know-More-News
Know More News Guest Link: Know More News with Adam Green
Adam Green's Documentary can be seen here: Subverting The Public
LINK: INTERNET FALSE FLAGS
The NSA Gave Israel Access to All US
Citizens' The Last American Vagabond Published on Jun 3, 2019 This is an excerpt of The Daily Wrap Up 6/2. Full Episode Can Be Seen Here: LINK: Subverting The Public
The Trump Administration Requests Permanent Reauthorization Of NSA Mass Spying Program
Full Episode Can Be Seen Here: Get a TLAV "Question Everything" T-Shirt or Sticker at: Try The SuperChat Alternative Where YouTube Does Not Get A Cut:
Breaking: NSA Gestapo Ban 1st Amendment, Confiscate Cameras
NSA data center employees surround Anthony Gucciardi and team to confiscate all cameras and attempt to delete all footage. This special breaking report broadcast live on air covers the event with HD footage. http://www.infowars.com/nsa-goons-con...
The National Security Agency was well aware it was committing violations of surveillance rules, according to newly declassified documents. The NSA self-reported the violations to a US intelligence court, and promised to enact new safety measures to prevent the violations from recurring. Despite the acknowledgement, the NSA broke its own rules again in 2009, according to FISA Court documents. These revelations come after similar ones in September that the NSA broke its own rules and mislead the FISA Court regarding bulk data collection.
Mastering The Human Domain
A closer look at the upcoming Jade Helm military exercise, specifically its “master the human domain” motto, reveals a larger agenda in regards to domestic policy. ...“They’re building an infrastructure of tyranny,” stated Infowars David Knight. “There’s a legal infrastructure with things like the NDAA, there’s a technical infrastructure with things like the capability to do dragnet surveillance, and then of course there is going to be a military and law enforcement infrastructure, and those are merging.”
Synopsis
Full Presentation
LINK: TOTAL POPULATION CONTROL
As the people of the world grapple with a pandemic that is demonstrably less deadly than originally reported, the public is being primed to accept an exponential increase in invasions of personal liberty and privacy. Every day the public grows more weary of lock downs which seem to never end, and the bankrupting of individuals and businesses around the world. Amidst the frustration and protest a solution is being presented. To return to normal, we are told, we must accept certain changes to how our world operates. Of course, this is actually a push to a “new normal” which will mark the world after COVID-19. Just like the attacks of September 11, 2001, there is the world we knew before, and there is the post-9/11 era. We are currently in the middle of the COVID-19 era and a shift to post-COVID19 life will not happen without the completion of local, state, national, and international programs which identify potential infectees, test them, and, if positive, quarantine them in their homes or other government facilities. This is what is known as a contact tracing program. You have likely heard the term in recent days and weeks because a number of local and state bodies within the United States are considering or already launching contact tracing programs. Nations like China, Singapore, India, South Korea, and Israel have implemented these programs but have also faced criticism from digital rights advocates for violations of privacy protections. So what exactly is contact tracing?Contact tracing is a process of identifying individuals who may have come into contact with an infected person, collecting information about their contacts, and then tracing the contacts of infected individuals. All persons who may have come into contact with an infected individual are tested for infection, treated for the infection, and their contacts traced as well. Regarding the COVID-19 pandemic, we are seeing calls for digital contact tracing using cell phones to notify individuals when they may have come into contact with an infected person or visited a hot spot of infection. Digital contact tracing apps use Bluetooth to track encounters, a move which is supposed to anonymize actual location data. Other forms of contact tracing apps involve the use of location data gathered from cellular networks. Additionally, tech giants Apple and Google have promised to help slow the spread of the virus with new tracking apps that the public can download to report themselves as infected. Using Bluetooth, the phones will warn app users when they are near an infected person or a hot spot. The programs will use data from Android and iPhone users who volunteer for the program later this month. Jennifer Granick, a surveillance and cybersecurity attorney with the American Civil Liberties Union told Politico that the joint effort between the tech companies “appears to mitigate the worst privacy and centralization risks.” However, “there is still room for improvement.” Microsoft is collaborating with the University of Washington on their own project which the university promotes as a privacy based contact tracing app. Researchers with the University of Washington and UW Medicine worked with volunteers from Microsoft to develop CovidSafe. The researchers stated that the app will alert users about potential exposure to COVID-19, but will do so without giving up anyone’s privacy. “With CovidSafe, all information is stored locally on your phone unless you choose to share that you’ve tested positive,” explained Justin Chan, a UW doctoral student in the Paul G. Allen School of Computer Science & Engineering. “Only then is your data sent to a secure server, and the app alerts anyone who has been nearby. After these notifications are sent, all the information is deleted.” CovidSafe is not the only attempt to build a privacy-based contact tracing program. In April, a team of researchers launched Coalition, a free contact tracing app designed to protect users’ privacy and protect communities during the COVID-19 crisis. Coalition claims to utilize secure Bluetooth Low Energy (BLE) and cryptography to protect a user’s identity by generating random anonymous IDs. The app uses Coalition’s Whisper Tracing, an open source privacy-first protocol that randomizes a user’s device identity and does not share identifiable information with the cloud. Building a Contact Tracing Army
New York Governor Andrew Cuomo recently announced efforts by NY state to hire thousands of contact tracers. The state’s contact tracing program is being developed with $10 million from former New York City Mayor Michael Bloomberg and support from Johns Hopkins University. Cuomo stated that applicants will need to go through a training program and pass an online exam before being granted the authority of contact tracer. The state’s program will involve identifying COVID-19 positive individuals, interviewing them about contacts in the previous two weeks, and then those contacts must isolate for two weeks. By late April, calls for contact tracing had grown so loud that Congressman John Garamendi introduced a bill that would “expand volunteer opportunities within AmeriCorps and the Federal Emergency Management Agency”. Garamendi is the Co-Chair of the AmeriCorps, a nationwide volunteer force created by former President Bill Clinton in 1993. The Orwellian bill – “Undertaking National Initiatives to Tackle Epidemic Act” or the UNITE Act – would allow AmeriCorps and FEMA to create a national contact-tracing corps. “The coronavirus pandemic has put an unprecedented strain on our society, and our
nation requires a significant scaling of testing and contact tracing in order to flatten the curve and lift
stay-at-home orders,”
Garamendi stated. Coincidentally, the UNITE Act lines up with recent calls for a contact tracing “army”. The South Carolina Department of Health and Environmental Control called for more contact tracers in the state. Dr. Joan Duwve, the Director of Public Health for DHEC, said being able to test someone rapidly was necessary. “We need an army of contact tracers to respond in a short time to someone who has a positive diagnosis,” Duwve said. On the opposite side of the country, California Governor Gavin Newsom has partnered with the University of California, Los Angeles and the University of California, San Francisco to train more than 3,000 employees to become “coronavirus detectives“. During a live streamed press conference Newsom described the efforts as a training academy designed to build an “army” of 20,000 people who can test, trace, and isolate people who may be infected. Sonia Angell, California Department of Public Health director and State Health Officer, also stated that the new contact tracing program will be connected to California’s existing digital disease surveillance platform. Angell claims the database will be confidential. The push for international contact tracing programs has also blossomed in nations like South Korea and China, who are praised for their aggressive approaches to slowing the growth of the virus. Forbes noted that South Korea has had a massive drop in COVID-19 diagnoses largely due to “mass rapid testing and comprehensive digitally-enabled contact tracing”. South Korea has also used GPS phone tracking, CCTV cameras, credit card transaction monitoring, and automated text alerts as part of a comprehensive universal contact tracing program. The Chinese government approach is what you would expect from a totalitarian communist state: an all encompassing app that pretty much “controls your life.” Bloomberg describes China’s contact tracing app as a “public-private ‘health code’ system” which issues one of three risk assessments in the form of a colored QR code. “A green QR code, which denotes a low risk of having the virus, is the general default, while coming into contact with an infected person can trigger a yellow code and a mandatory quarantine. Red is for a likely or confirmed case,” Bloomberg reported. It does not take an extremely paranoid mind to see how this system could be easily abused. The Indian government recently launched their contact tracing app – Aarogya Setu – which quickly became the fastest downloaded app on record, with more than 83 million users. Although India is not the first nation to implement a nationwide contact tracing program, the nation lacks strong privacy and data protection laws for its more than 1.3 billion citizens. The Guardian reported that the pandemic is being “used as a pretext to erode privacy and freedom of speech in the name of ‘winning the war’ against coronavirus.” In April The Guardian revealed that a draft government memo explained how the data gathered by the contact-tracing app could be “de-anonymized” by government officials. Israel’s attempted grab for tyrannical health surveillance powers were recently hampered by a decision from the Supreme Court which banned the intelligence community from tracing the phone location of those infected with COVID-19. The Israeli Shin Bet service was given emergency powers through the end of April before the court warned of a “slippery slope” where the surveillance tool could be used against innocent individuals. Whitney Webb recently reported that at least three tech companies involved in the build out of the “coronavirus surveillance system” have connections to Israel’s government and the usual Big Tech players. Following The Orders of the WHO
In early April, Dr. Michael Ryan, the head of the World Health Organization’s team responsible for the international containment and treatment of COVID-19, called for looking into families to find potentially sick individuals and isolate them from their families. “Due to lock down, most of the transmission that is actually happening in many countries now is happening in the household at a family level,” Ryan stated. “In some senses, the transmission has actually been taken off the streets and pushed back into family units… Now we need to go and look into families, and find those people who are sick and remove them and isolate them in a safe and dignified manner.” Ryan was also involved in the now-infamous Event 201, a global pandemic simulation, conducted on October 18, 2019, funded by the Bill and Melinda Gates Foundation, the World Economic Forum, and John Hopkins University Center for Health Security. Ryan’s bio states that “from November 2013 to October 2014 he worked with GPEI as Middle East Polio Response Coordinator” and partnered with the Bill and Melinda Gates Foundation (among others) for a vaccination program which reached 25 million children in eight target countries as part of 44 mass polio vaccination campaigns. Ironically enough, the WHO released a document in 2019 which states that under no circumstances should contract tracing be used. The document, first reported on by independent researcher Kenny Palurintano, details the WHO’s views on Non-pharmaceutical intervention (NPI) in response to a pandemic. In section 6.1, “Contact Tracing,” under “quality of evidence”, it states, “There is a very low overall quality of evidence that contact tracing has an unknown effect on the transmission of influenza.” Additionally, under the “Executive Summary”, in Table 1, the WHO lists contact tracing under the heading “Not Recommend In Any Circumstances”. Despite the WHO’s own documents denying the validity of contact tracing, officials in Ventura County are heeding the call of WHO official Dr. Michael Ryan. At a May 4 press conference, Ventura County Public Health Director Dr. Robert Levin said those who live in homes where they could expose family members to COVID-19 could be removed from their homes and moved into other health facilities. “We also realize that as we find more contacts, some of the people we find are going to have trouble being isolated. For instance, if they live in a home where there is only one bathroom and there are three or four other people living there, and those people don’t have COVID infection, we’re not going to be able to keep the person in that home,” Levin stated. “Every person who we’re isolating, for instance, needs to have their own bathroom. And so we’ll be moving people like this into other kinds of housing that we have available.” The Ventura County Public Health board did not elaborate on what other kinds of housing might be made available to those unable to quarantine at home. If there is a silver lining to the growing support for contact tracing, it might be the public’s own hesitance to join. According to Forbes, nation-states need about 60 percent of their population to adopt and regularly use the tool for it to be effective. Forbes reports that most cities are not likely to achieve 60% or even 40% compliance. Unfortunately, Forbes reminds us, “It’s a relentless fight. And it takes an army of tracers.” Forbes also notes that cities will need to “force changes of behavior” before reopening society. “Contact-tracing apps are being seen as one of the conditions of ending lockdowns—mandating and enforcing their use might become a logical next step.“ How exactly the cities, states, and nations will enforce the use of contact tracing apps remains to be seen, but we are already seeing a rise in reports of arrests of individuals who violate orders to close businesses, stay home, and practice social distancing. What should we expect to see when an individual or an entire community chooses to opt-out of contact tracing surveillance programs? It is important to understand that contract tracing is only one part of an overall strategy which poses a danger to liberty and privacy. In addition to creating mobile apps which snitch on you, Apple, Facebook and Google are also sharing data with the government to help determine if the public is following social distancing guidelines. MIT Technology Review reported that at least one company is selling an app that uses machine learning Artificial Intelligence to monitor social distancing. Meanwhile, Reuters reported that Amazon is using similar software to enforce social distancing between their warehouse staff. There are also reports of “pandemic drones” flying above the skies of Connecticut and Maryland to monitor social distancing and take temperatures. Together these technologies represent the foundation of the Technocratic State, built on top of the fears of a public which has been conditioned to accept any and all relief from the terrifying round-the-clock coverage of the COVID-19 pandemic. If the public accepts the COVID1984 Technocracy in the name of “getting back to normal” it’s likely the world we have known will be regarded as a relic of a past era, a quaint idea of what life was like and what it could be, if only the public could defeat the new invisible enemy, COVID19. However, it’s important to understand the institutions which are benefitting from the current pandemic. Only by acknowledging the true power players – those who maneuver behind the scenes to profit and enslave – can the free hearts and minds of the world defeat the true enemy: COVID-1984.
NSA knew it was breaking its own spying rules The National Security Agency was well aware it was committing violations of surveillance rules, according to newly declassified documents. The NSA self-reported the violations to a US intelligence court, and promised to enact new safety measures to prevent the violations from recurring. Despite the acknowledgement, the NSA broke its own rules again in 2009, according to FISA Court documents. These revelations come after similar ones in September that the NSA broke its own rules and mislead the FISA Court regarding bulk data collection. RT's Ameera David has the reaction from the FISA Court that the NSA overstepped its boundaries and ignored privacy protections.
Obama Fears Arrest and is Running Scared From NSA Scandal [VID] Obama is so desperate to
brush aside the governments illegal NSA spying activity that he compared it to the actions of patriot Paul
Revere.
The government's defense of constant surveillance of the American public has reached a new level of absurdity CEO Billionaires Defend NSA
The government's defense of constant surveillance of the American public reached a new level of absurdity when Obama compared Paul Revere to the NSA. Now it's time for the corporate billionaires to defend what their puppet Obama can't. Enter Bill Gates and Marc Andreesen to tell that we need to trust the NSA and we're too stupid to understand the technology. William Binney, former Technical Director of the NSA worldwide understood the technology and has been telling us that the NSA is breaking the law.
**A MUST-SEE** Glenn Greenwald "The Goal Of The U.S.
Government Is
You Won’t BELIEVE What’s Going On with Government Spying on Americans New Revelations Are Breaking Every Day
Washington’s Blog
Revelations about the breathtaking scope of government spying are coming so fast that it’s time for an updated roundup: - Just weeks after NSA boss Alexander said that a review of NSA spying found not even one violation, the Washington Post published an internal NSA audit showing that the agency has broken its own rules thousands of times each year - 2 Senators on the intelligence committee said the violations revealed in the Post article were just the “tip of the iceberg” - Glenn Greenwald notes: “One key to the WashPost story: the reports are internal, NSA audits, which means high likelihood of both under-counting & white-washing”.(Even so, the White House tried to do damage control by retroactively changing on-the-record quotes) - The government is spying on essentially everything we do. It is not just “metadata” … although that is enough to destroy your privacy - The government has adopted a secret interpretation of the Patriot Act which allows it to pretend that “everything” is relevant … so it spies on everyone - NSA whistleblowers say that the NSA collects all of our conversations w ord-for-word - It’s not just the NSA … Many other agencies, like the FBI and IRS – concerned only with domesticissues – spy on Americans as well - The information gained through spying is shared with federal, state and local agencies, and they are using that information to prosecute petty crimes such as drugs and taxes. The agencies are instructed to intentionally “launder” the information gained through spying, i.e. to pretend that they got the information in a more legitimate way … and to hide that from defense attorneys and judges - Top counter-terror experts say that the government’s mass spying doesn’t keep us safe - Indeed, they say that mass spying actually hurts U.S. counter-terror efforts. - They say we can, instead, keep everyone safe without violating the Constitution … more cheaply and efficiently than the current system - There is no real oversight by Congress, the courts, or the executive branch of government. And seethis and this. - Indeed, most Congress members have no idea what the NSA is doing. Even staunch defenders of the NSA now say they’ve been kept in the dark - A Federal judge who was on the secret spying court for 3 years says that it’s a kangaroo court - Even the current judges on the secret spying court now admit that they’re out of the loop and powerless to exercise real oversight - A former U.S. president says that the spying program shows that we no longer have a functioning democracy - The chairs of the 9/11 Commission say that NSA spying has gone way too far - Top constitutional experts say that Obama and Bush are worse than Nixon … and the Stasi East Germans - While the government initially claimed that mass surveillance on Americans prevented more than 50 terror attacks, the NSA’s deputy director John Inglis walked that position back all the way to saying that – at the most – one (1) plot might have been disrupted by the bulk phone records collection alone. In other words, the NSA can’t prove that stopped any terror attacks. The government greatly exaggerated an alleged recent terror plot for political purposes (and promoted the fearmongering of serial liars). The argument that recent terror warnings show that NSA spying is necessary is so weak that American counter-terrorism experts have slammed it as “crazy pants” - Even President Obama admits that you’re much less likely to be killed by terrorists than a car accident. So the government has resorted to lamer and lamer excuses to try to justify mass surveillance - Experts say that the spying program is illegal, and is exactly the kind of thing which King George imposed on the American colonists … which led to the Revolutionary War - The top counter-terrorism Czar under Clinton and Bush says that revealing NSA spying programs does not harm national security - The feds are considering prosecuting the owner of a private email company – who shut down his business rather than turning over records to the NSA – for refusing to fork over the information and keep quiet. This is a little like trying to throw someone in jail because he’s died and is no longer paying taxes - Whistleblowers on illegal spying have no “legal” way to get the information out - There are indications that the government isn’t just passively gathering the information … but is actively using it for mischievous purposes - Spying started before 9/11 … and various excuses have been used to spy on Americans over the years - Governments and big corporations are doing everything they can to destroy anonymity - Mass spying creates an easy mark for hackers. Indeed, the Pentagon now sees the collection of “big data” as a “national security threat” … but the NSA is the biggest data collector on the planet, and thus provides a tempting mother lode of information for foreign hackers - Mass surveillance by the NSA directly harms internet companies, Silicon Valley, California … and theentire U.S. economy. And see these reports from Boingboing and the Guardian - IT and security professionals are quite concerned about government spying - Some people make a lot of money off of mass spying. But the government isn’t using the spying program to stop the worst types of lawlessness - Polls show that the public doesn’t believe the NSA … and thinks that the government has gone way too far in the name of terrorism - While leaker Edward Snowden is treated as a traitor by the fatcats and elites, he is considered a hero by the American public - Congress members are getting an earful from their constituents about mass surveillance - The heads of the intelligence services have repeatedly been caught lying about spying. And even liberal publications are starting to say that Obama has been intentionally lying about spying - Only 11% of Americans trust Obama to actually do anything to rein in spying - A huge majority of Americans wants the director of intelligence – Clapper – prosecuted for perjury - While the Obama administration is spying on everyone in the country – it is at the same time the most secretive administration ever (background). That’s despite Obama saying he’s running the most transparent administration ever - A Congressman noted that – even if a mass surveillance program is started for good purposes – it will inevitably turn into a witch hunt - Surveillance can be used to frame you if someone in government happens to take a dislike to you - Government spying has always focused on crushing dissent … not on keeping us safe - An NSA whistleblower says that the NSA is spying on – and blackmailing – top government officials and military officers (and see this) - High-level US government officials have warned for 40 years that mass surveillance would lead to tyranny in America - A top NSA whistleblower says that the only way to fix things is to fire all of the corrupt government officials who let it happen. As the polls above show, the American public is starting to wake up to that fact This article was posted: Saturday, August 17, 2013 at 5:09 am
NSA Whistleblower: Everyone is Under Virtual Surveillance, All Info Stored, No Matter The Post
NSA Whistleblower Reveals Planned Police State
David Knight is joined by Former NSA official and whistleblower William Binney to discuss the
latest developments on the intelligence agency's domestic spying under the guise of national security.
NSA Whistleblower: "National Security is A Scam"
David Knight and William Binney continue on the topic of the current police state and the
slow destruction of the Constitution as we know it.
NSA vs USA: Total surveillance zooms-in on Americans
Ever evolving high-tech gadgets and the Internet have given Big Brother a peep hole into the lives of everyday Americans. Now, without the hassle of planting bugs or breaking and entering, the government can monitor virtually anything it wants.
Google & NSA Relationship Under Wraps
If the biggest internet company and the biggest surveillance agency work together do you think we, the public, have a right to know? Well the courts don't think so. Alyona talks to activist at the Electronic Frontier Foundation, Trevor Timm about the NSA and Google's secret relationship.
NSA Illegally Spying on Everyone: Craig B. Hulet Reports
Whistle Blower Threatened with 35 Years in Prison, Warns of Developing Tyranny Thomas Drake blew the whistle on a massive domestic information gathering scheme and was called "an enemy of the state" (speech at Sam Adams Awards)
Telecom Insider: Everyone Is Wiretapped!
Rob Dew speaks with Critical Infrastructure Consultant James Knox about the NSA and
History... The Origins of the U.S. Intelligence Community & Why It Spies on Americans
Tonight, on History So it doesn't Repeat: We ask the question: Is America safer, now that we're openly being spied on? We'll discover how to check our premises, and peer into the origins, form, and function of the intelligence Community. By studying those who spy on us, we'll uncover the root-causes of the War on Terror; and you will have the facts to help end it. Learning's the Answer, What's the Question? It's all coming up next, on History So It Doesn't Repeat.
Exposing 'Five Eyes' Global Surveillance Cabal Big Brother Watch Description: Abby Martin takes a closer look at a recent NSA leak which links the US, UK, Australia, Canada and New Zealand as an international intelligence partnership focused on surveillance of each other's citizens.
NSA Spying: False Hope vs. Real Solutions (IMPORTANT - PLEASE SHARE)
In this special edition of The Boiling Frogs Post Eyeopener report, James introduces new members of the
irate minority to the problem, as well as the false hopes (and real solutions) that are available to
address that problem.
Podcast: Play in new window | Download Running Time: 1:00:01
Description:This week on The Corbett Report we present a special audio and video edition of the podcast/vodcast. This week we delve into the true history of the illegal NSA wiretap program and how it connects to the bigger picture of government surveillance. Documentation
Info-graphic: NSA Is A Billion Times More Expansive Than The Stasi
US agency would need a facility the size of Europe to store physical copies of information it will hold
Steve Watson A stunning info-graphic put together by a German data company reveals just how expansive the NSA’s data retention program has become. In the wake of the Snowden revelations, eyes have been trained on the NSA and its almost completed new facility in the Utah desert. the NSA’s warrantless wiretapping program has grown in gargantuan proportions and now intercepts 1.7 billion US electronic communications every single day. Those communications will soon all be funneled through the top secret $2 billion spy center, which the NSA has refused to provide Congress with details of. Comparing the NSA to the East German Stasi, experts at Open Data City in Berlin, decided to visualize the scope of both spy agencies, to make a point of how much further advanced the NSA is. The shaded area on the left shows how much physical space the Stasi encompassed in Berlin, then compares the space the NSA would need if it had physical copies of all the information it is capable of storing.
While the Stasi kept all it’s files in physical form, as revealed by NSA whistleblower William Binney, the NSA data center in Utah will be capable of storing 5 zettabytes of digital information (5 billion terabytes). “They would have plenty of space with five zettabytes to store at least something on the order of 100 years worth of the worldwide communications, phones and emails and stuff like that,” Binney asserts, “and then have plenty of space left over to do any kind of parallel processing to try to break codes.” Cisco quantifies a zettabyte as the amount of data that would fill 250 billion DVDs. Open Data City notes that a filing cabinet requires 0.4 m square, and can hold about 60 folders containing roughly 30,000 pages of paper, which equates to somewhere in the region of 120 MB of data. Given these facts, the Utah data center, if it were to store printed copies of all the information it can hold, would consume about 17 million square kilometers of space. The shaded area in the image below shows you how much space that is. It pretty much covers the entire continent of Europe.
In comparison, the Stasi Records Authority spanned a mere 200 kilometers at its facility in Berlin. Consequently, the NSA can hold nearly 1 billion times more data than the Stasi could. Of course, there is no need to worry, for the NSA vows that it only targets terrorists and extremists, just liked the Stasi did. —————————————————————- Steve Watson is the London based writer and editor for Alex Jones’ Infowars.com, and Prisonplanet.com. He has a Masters Degree in International Relations from the School of Politics at The University of Nottingham, and a Bachelor Of Arts Degree in Literature and Creative Writing from Nottingham Trent University. This article was posted: Friday, July 5, 2013 at 11:59 am Tags: big brother, domestic spying
DHS, CYBERCOM: Government & private sector “must” share data to prevent cyber threats “Fascism should more appropriately be called Corporatism because it is a merger of state and corporate power.” -Benito Mussolini
Aaron Dykes & Alex Jones The takeover of the Internet is literally a fascist partnership between Google, the NSA, US CYBERCOM and other key entities. In recent weeks, a court refused to disclose the links between Google and the NSA, but obviously it confirms the important bleed over that has long been documented and exposed. General Keith Alexander, head of both the NSA & CYBERCOM, who meets annually at Bilderberg with the likes of Google’s Eric Schmidt, Microsoft’s Craig J. Mundie (and former CEO Bill Gates), Facebook’s founders & funders and others, recently testified to the Senate Armed Services Committee about US CYBER COMMAND’s mission.
[vid]
Gen. Alexander endorsed the Department of Homeland Security’s Blueprint for a Cyber Secure Future, which he helped write and give feedback on. “We welcome and support new statutory authorities for DHS that would ensure this information sharing takes place; an important reason why cyber legislation that promotes this sharing is so important to the nation.” Alexander further stated, “Foundational to [CYBERCOM's mission] is the information sharing that must go on between the federal government and private sector, and within the private sector, while ensuring measures and oversight to protect privacy and preserve civil liberties.” Aside from the recognition of civil liberties that is merely for public consumption, this is a stark admission of the massive data theft that has been going on unchecked for sometime. Such data mining, along with “identity-based access controls to services” (eerily close to fellow Bilderberger Neelie Kroes, of the EU Commission, would supposedly allow the prevention and detection of cyber crimes, hack attacks and any plans for “big” events like a (cyber) terror attack. To prepare for such paralyzing and potentially catastrophic events, CYBERCOM has done what it does best– go on the offensive. Information Week reports:
Gen. Alexander further bragged about CYBERCOM’s first major tactical exercise, dubbed “CYBER FLAG”, in which operators “engaged in realistic and intense simulated cyber combat against ‘live’ opposition.” Top brass at the Pentagon and numerous intelligence agencies, who are also involved in CYBERCOM according to Alexander, also participated in the multi-day exercise. Alexander cautioned that “CYBER FLAG was no mere drill, but a training exercise for those necessarily engaged in cyber operations now.” Wow. US CYBERCOM, which is literally housed inside the National Security Agency (NSA), has only been in existence for two years and only operational for a little over a year, yet is eager to expand its powers in effort to guard the nation, its government agencies and peoples from cyber threats far and wide. Gen. Alexander cited numerous attempts to bring down military networks and those of their contractors. Hackers groups including Anonymous and LulzSec made 2011 the “Year of the Hacker,” Alexander told Congress, and things are clearly just getting started. Stuxnet (admittedly launched jointly by the U.S. & Israel) and other incidents have made that clear.
Every Six Hours, the NSA Gathers as Much Data as Is Stored in the Entire Library of Congress
Dan Nosowitz writes on Popular Science:
Utah Welcomes NSA Mega-Snoop Center Kurt Nimmo Utah will be home to NSA’s mega-surveillance program under the aegis of the formerly secret Comprehensive National Cyber-security Initiative.
“Today’s groundbreaking for a $1.5 billion National Security Administration data center is being billed as important in the short term for construction jobs and important in the long term for Utah’s reputation as a technology center,” reports Deseret News today. “This will bring 5,000 to 10,000 new jobs during its construction and development phase,” boasted Sen. Orrin Hatch, R-Utah. “Once completed, it will support 100 to 200 permanent high-paid employees.” The new “data center” will probably function as the Department of Homeland Security’s “Social Networking Monitoring Center,” an effort outed late last year by the Electronic Frontier Foundation. The EFF inititated a FIOA request and received documents revealing that the DHS vacuums up data and “items of interest” on the American people. The DHS used the system to monitor social media networks during Barry Obama’s inauguration. “DHS collected a massive amount of data on individuals and organizations explicitly tied” to the inauguration, according to the documents obtained by the EFF. The DHS-NSA collaboration to surveil the American people is part of National Security Presidential Directive 54/Homeland Security Presidential Directive 23, signed by Bush in early 2008. “This initiative created a series of classified programs with a total budget of approximately $30 billion. Many of these programs remain secret and their activities are largely unknown to the public,” reports Public Intelligence. The Comprehensive National Cybersecurity Initiative scheme is a textbook example of fascism. CNCI is described as “an effort to encourage information sharing between the public and private sector called ‘Project 12′,” in other words an effort by the government roll over the private sector. PI “recently acquired the key report from the Project 12 meetings: Improving Protection of Privately Owned Critical Network Infrastructure Through Public-Private Partnerships. This 35-page, For Official Use Only report is a guide to creating public-private partnerships that facilitate the implementation of ‘actionable recommendations that [reflect] the reality of shared responsibility between the public and private sectors with respect to securing the nation’s cyber assets, networks, systems, and functions’.” Project 12 emphasizes the “promotion of public-private partnerships that legalize and facilitate the flow of information between federal entities and private sector critical infrastructure, such as telecommunications and transportation.” So-called public-private partnerships are based on the economic model proposed by Italy’s dictator, Benito Mussolini, the former radical socialist and the grand daddy of fascism. “The ultimate goal of these partnerships” an analyst writes, “is not simply to increase the flow of ‘threat information’ from government agencies to private industry, but to facilitate greater ‘information sharing’ between those companies and the federal government.” Cyber-security is the next phase in the war on terror, in actuality a war on the American people, or more specifically on American citizens who disagree with the government and threaten to overturn the statist apple cart through political activism. The Stasi-like apparatus to be built for the NSA and DHS by the death merchant Raytheon’s Intelligence and Information Services division “would rely on a set of sensors deployed in computer networks for critical infrastructure that would be triggered by unusual activity suggesting an impending cyber attack,” according to the Wall Street Journal. “The overall purpose of the [program] is our Government… feel[s] that they need to insure the Public Sector is doing all they can to secure Infrastructure critical to our National Security,” Tim Shorrock wrote for CorpWatch last year. As noted by the Wall Street Journal, the the program – known as Perfect Citizen and described as the NSA’s perfect spying tool – will have major implications “beyond the critical infrastructure sector,” in other words it will transcend so-called cybersecurity and engineered threats absurdly hyped by the government and its Mockingbird propaganda asset, the corporate media. Perfect Citizen – described unabashedly as Big Brother by Raytheon – also serves as a perfect excuse to expand the surveillance and control grid to privately owned and operated networks. The NSA and DHS are not particularly interested in al-Qaeda’s cartoonish phantom hackers in caves or threats supposedly posed to our not so susceptible infrastructure by China or Russia. The NSA is more interested in tracking and snooping antiwar and peace activists than some kid in Latvia – as Jay Rockefeller famously put it – meddling with power grids not hooked up to the internet. In addition to suspect enemies of the state protesting against illegal and immoral wars, the NSA has expended a vast amount of resources in its effort to surveil average Americans. “The NSA program reaches into homes and businesses across the nation by amassing information about the calls of ordinary Americans — most of whom aren’t suspected of any crime,” USA Today reported in 2006. USA Today misses the point. The idea is not to track down criminals and supposed terrorists, but to track and trace the American people and keep tabs on their political activity. If need be, this political activity can be “neutralized,” as J. Edgar Hoover put it when he described the FBI’s COINTELPRO, the illegal covert program to destabilize and render ineffective political movements and on occasion assassinate their leaders. Job One for government is to protect at all cost its monopoly on power. Osama bin Dead and his gaggle of CIA trained patsies do not threaten the fascist partnership between the government and multinational corporations – politically active citizens do.
Mass Government Surveillance Dragnet Goes Into OverdriveFBI unit to spy on all communications, including skype conversations Steve Watson  As if the government were not engaging in enough surveillance of law
abiding Americans already, two major developments just ensured that the snooping will increase
exponentially. As if the government were not engaging in enough surveillance of law
abiding Americans already, two major developments just ensured that the snooping will increase
exponentially.
Firstly, the FBI is about to launch a huge new surveillance unit that will have the ability to monitor all internet and wireless communications, including internet Skype conversations. The incredibly Orwellian titled Domestic Communications Assistance Center, will “assist” local, state, and federal law enforcement agencies in spying on the American people. After reviewing a multitude of government documents and interviewing sources involved with the FBI unit, Declan McCullagh of CNet reports:
McCullagh notes that the unit has been in the pipeline for years and that spearheading it will be the FBI’s massive wiretapping project, which was allocated $54 million by a Senate committee last month. McCullagh has also extensively reported on the FBI’s push to make it law to require social-networks and providers of VoIP, instant messaging, and Web e-mail to build in backdoors for government surveillance. The Bureau is reportedly urging Internet and communications companies not to oppose the move. We want to “be able to obtain those communications,” FBI Director Robert Mueller said last Wednesday. “What we’re looking at is some form of legislation that will assure that when we get the appropriate court order that those individuals — individual companies are served with that order do have the capability and the capacity to respond to that order.” The second major development on the government surveillance front is that a Senate Panel has voted this week to extend the government’s authority to engage in warrantless wiretapping. The Senate Select Committee on Intelligence voted to extend through to June 2017 the 2008 provision of the Foreign Intelligence Surveillance Act (FISA). The provision would allow the government to continue monitoring e-mails and phone calls of those it considers to be “terrorism suspects.” The Washington Post reports:
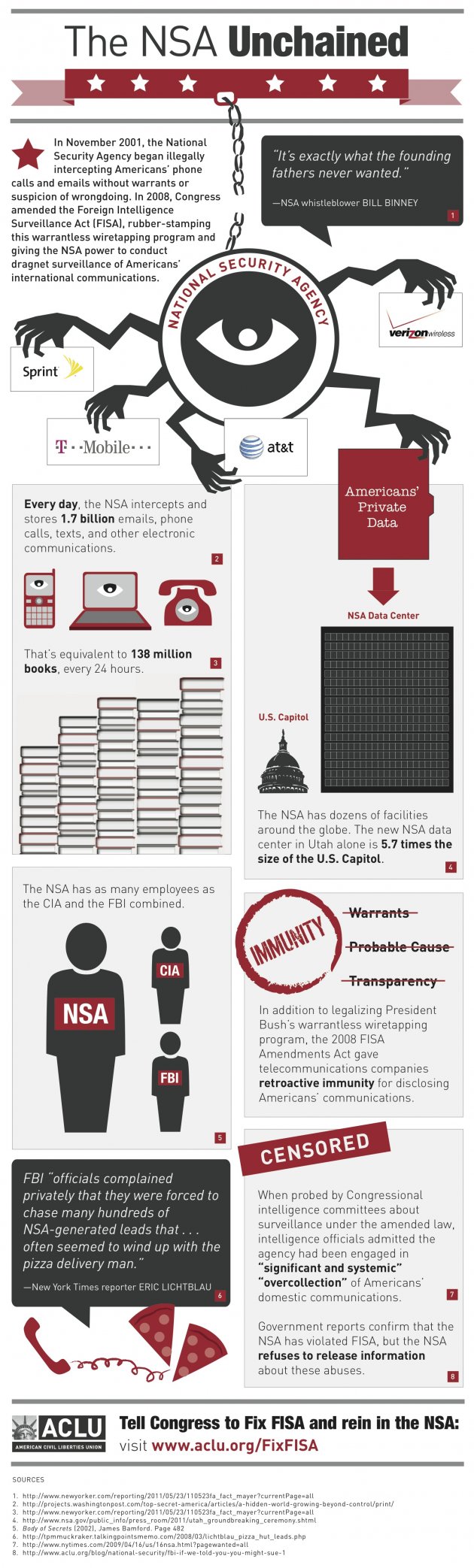
The FISA provision introduced in 2008 was merely a confirmation of activity that government spy agencies, such as the NSA, have been engaging in for years. The ACLU recently released an infographic (below) detailing how the NSA’s warrantless wiretapping program has grown in gargantuan proportions and now intercepts 1.7 billion US electronic communications every single day. Those communications will soon all be funneled through the top secret $2 billion spy center in the Utah desert, which the NSA has refused to provide Congress with details of. The surveillance dragnet just got a hell of a lot bigger, and rest assured that while the government says its official targets are “terrorists”, snoops are using these powers to go after Americans exercising their constitutional rights.
Obama: Pay no attention to the massive NSA complex under the mountainsObama employs tried and true “gaslighting” technique
Adan Salazar
As much as we’d like to believe in president Obama’s reassurances that nobody is listening to our phone calls, what we’ve gleaned from whistleblowers in the past tells a very different story.
For instance, National Security Agency whistleblower William Binney, last year stated,
Binney has direct insider knowledge, having worked for the NSA for a staggering 32 years as technical director. Binney says he built the back-end for a program that has since been redirected towards the American people, tracking and logging every citizen’s phone calls, texts, emails, Google searches, and even social network history. The central hub for all recorded activities is said to be a data storage facility in Bluffdale, Utah with, reportedly, the capacity to store 100 years worth of data. The London Telegraph even produced a mini-documentary on the subject titled, “The Program (Stellar Wind),” a project they introduced as follows: “Following 9/11, the National Security Agency began a top-secret surveillance program to spy on U.S. Citizens without warrants.”
And again this year, an insider let slip yet another bombshell. When the FBI began investigating bombing suspect Tamerlan Tsarnaev’s girlfriend Katherine Russell’s possible involvement in the Boston Marathon bombing, a former FBI counterterrorism agent blurted out on CNN’s Erin Burnett Show that the government has the capability to go back and find out exactly what was said in conversations.
Here’s the exchange between former FBI agent Tim Clemente and Burnett, courtesy of Glenn Greenwald:
Of course, Obama is just the current frontman, teleprompter-reading puppet. This form of invasive spying has been ongoing since 9/11, started under Bush and merely passed on to Obama. Plus, if he were to openly admit every American’s electronic data has, for a long time now, been monitored, it would possibly put a rather large snag in their multi-billion dollar intelligence front. And besides, what’s a president for if not to reassure everyone that everything is perfectly alright? Obama employs tried and true “gaslighting” technique “That’s not what this program is about,” Obama said. But according to William Binney, that’s exactly what it’s about. Obama, in his official capacity, is engaged in desperate damage control and is employing a psychological technique known as gaslighting, whose meaning derives from a 1938 stage play. Gaslighting is when you’re told false information repeatedly, over and over again until you start to doubt your own perceptions and memory and start believing what you’re being told. For example, a person walks up to you and asks if you’re OK because you just took a spill. You’re sure you’ve been standing upright the entire time, but the person insists you’ve just had a fall and persists in asking if you’re OK until you concede that you must have fallen and finally thank the person who walked up to check on you. Another form of this also occurs in George Orwell’s novel 1984 – which is highly recommended reading now more than ever – when the lead character Winston, after a long bout of imprisonment and refusal to cooperate, began writing the words, “Freedom is slavery,” and “two and two make five,” whereas prior to his enslavement he knew these things to be contradictory or outright false. We are now very much in Winston’s shoes, as we are expected to digest everything the president spews from on high, unquestionably and without contemplation or hesitation. Pay no mind that the government is actively soiling the Constitution and breaking all sorts of laws. It isn’t happening. You should reject voices that warn tyranny is lurking around the corner, remember?
What’s Wrong With the NSA Collecting Your Phone Records?
Michael S. Rozeff
Verizon is being forced by the government to disclose telephone records of all of its customers. Those of us who want our call records to be private are being forced to reveal them to the government. We can’t keep them private even if we want to. What is wrong with the government spying on us in this way? Murray Rothbard has made a clear and correct libertarian case against any compulsory speech. As I understand this, our thoughts are our own. They are private. Our imaginings are our own. Our fantasies are our own. We can imagine the most heinous crimes and plan them out in our minds if we wish. We can have any sexual fantasies we wish to have. We can indulge in as many hateful, malevolent and spiteful thoughts as we wish. We can have private saintly wishes, fond hopes, mistaken views, ill-formed ideas, flashes of genius, communications with God or with the devil, atheistic thoughts, artistic ideas, or superstitions. I hardly scratch the range of what we can think. It is that vast. If it is illegitimate, in the libertarian world explained by Rothbard, to use force against a non-aggressor, then no one has a right to make us talk or to make us reveal our thoughts because our thoughts are not aggressions. That’s one argument. Here’s a second argument. If force is allowable to be used on people’s thoughts, two kinds of results will rise in frequency. First, people will be forced to reveal thoughts that they don’t want revealed because they consider them damaging to themselves or others. People simply could not get along with one another if what people thought of each other or knew about each other were revealed or could be revealed or were made to be revealed. Society would break down. Second, people will be forced not to reveal thoughts that they want to be revealed, such as new ideas that go against conventional wisdom. Think of the suppression and persecution of Galileo. Both kinds of results cause costs to the person and society. The right to think and speak and the concomitant right to think and not speak limit these two costs. Free speech extends to related activities. If you have a right to speak or not to speak, then you have a right to commit your thoughts to paper and keep the paper private. You have a right to communicate your thoughts to others and keep that contact private. Speech extends to joint communications with others and to the making of joint plans. It extends to using various means of communication, such as paper and electronic devices. These actions are natural extensions of free speech and the same libertarian-law reasoning applies. You can privately conspire by yourself or with others (plan) to build the most marvelous energy-saving device, or you can privately conspire (plan) to dope a horse in a horse race. The latter cannot be a crime because you haven’t actually doped the horse. Furthermore, you can change your mind and not dope that horse. Neither one of these private plans, for good or ill, invades the rights of others. Both are exercises of one’s rights. Yes, it is no crime to plan a crime, by this reasoning. To say otherwise opens up the Pandora’s Box of controlling all speech (and associated behavior) in the name of preventing crime and of finding people guilty of thought crimes, as opposed to actual crimes. This is rank totalitarianism. The government engages in this via conspiracy laws. Verizon is an intermediary. The government is essentially making you and me send them a record of our calls. I’ve made three arguments against this, all of them viewing this as going against free speech and as an invasion of privacy. First, under libertarian law reasoning, making you reveal your records when you have committed no crime is an aggression and illegitimate. Second, if such aggression is permitted, it results in two serious costs, which are associated with revealing speech that people want kept private and suppressing speech that people want made widely known. Third, such aggression is part and parcel of a totalitarian mindset that, by extension, attempts to control speech as a preventive measure and find people guilty of thought crimes that have aggressed against nobody. What the government is doing to Verizon’s customers is wrong for these reasons. The government argues that it’s going to use the data to catch terrorists or potential terrorists who intend to violate rights of innocent people. The government is for sure invading our free speech rights against the slim possibility that terrorists will invade our lives. Which of these is a greater threat to us? Our own government’s totalitarian moves in the past 10 years or potential terrorists who are being encouraged by our own government’s activities overseas? Can any rights ever be secured by a government that believes it is proper for it to invade some or many rights in order to secure others? Isn’t this yet another Pandora’s Box? Isn’t a government with this kind of power wide open to invading any rights it pleases?
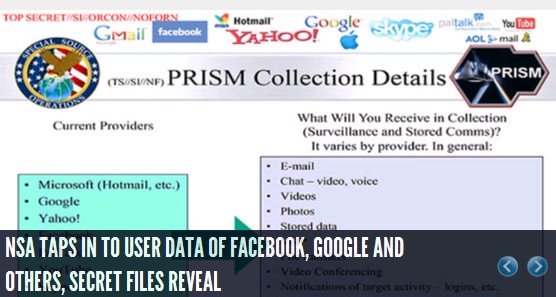
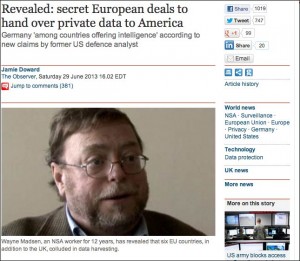
NSA taps in to user data of Facebook, Google and others, secret files reveal
NSA Whistleblower Wayne Madsen Exposed NSA’s International Spying Back in June Madsen’s report breaking US spying on Europe killed by Guardian
Adan Salazar
Long before NSA contractor Edward Snowden’s revelations regarding German Chancellor Angela Merkel emerged, investigative journalist and former NSA technician Wayne Madsen had relayed key intel based on information obtained through confidential sources outlining the NSA’s secret backroom deals with several European countries. For 12 years, Madsen worked with the NSA and witnessed firsthand how Americans’ private data got pilfered, sifted through and logged on a daily basis. He has since taken up post as one of the most influential muckraker journalists of our time, working to shed light on the surveillance state’s piecemeal deconstruction of the Constitution, as well as expose corruption of the beltway elite. More recently, Madsen’s name was in the news, ironically, when it was cut from the news.
[vid]
Following the hailstorm of media attention generated by Snowden’s PRISM leaks, Madsen said he felt obliged to speak out after seeing world leader after world leader feign incredulity at the NSA spying news.
Click to enlarge. According to Business Insider, Doward wrote:
“I can’t understand how Angela Merkel can keep a straight face – demanding assurances from Obama and the UK – while Germany has entered into those exact relationships,” Madsen told PrivacySurgeon.org’s Simon Davies back in June. “She’s acting like inspector Reynaud in Casablanca: ‘I’m shocked – shocked – to find gambling going on here.’” London’s prestigious newspaper drummed out both an online and a print version of the scoop, both of which underwent cutting room floor executions, but not before dozens of news outlets had already latched onto the story and either reprinted or reported on it. Now, reports that the German Chancellor’s phone may have been tapped have once again surfaced, and right on cue Germany is pretending they know nothing. But exposing collusion on international spy networks is just a run-of-the-mill occurrence for Madsen, who’s been at it for longer than two decades. In 1999, Madsen revealed what “may be the greatest intelligence scam of the century: For decades, the US has routinely intercepted and deciphered top secret encrypted messages of 120 countries.” In 2009, he shed light on the NSA’s “Q group,” a counter-intelligence security group comprised of about 1,000 agents working with the FBI and local law enforcement to prosecute and harass journalists and federal whistleblowers, especially those working to tie the federal government to the attacks of 9/11. His information came from leaked documents uncovered in 2005 regarding a program known as “Firstfruits,” which detailed how, during the Bush administration, the NSA “eavesdropped on the private conversations and e-mail of its own employees, employees of other U.S. intelligence agencies — including the CIA and DIA — and their contacts in the media, Congress, and oversight agencies and offices.” In 2008, sources told Madsen that one of the alleged customers of “DC Madam” Deborah Jeane Palfrey, who ran an upscale escort service in Washington DC for thirty years, was possibly former Vice President Dick Cheney, a statement Palfrey could neither deny nor confirm. Following Madsen’s bombshell, Palfrey “committed suicide,” mere months after telling the Alex Jones Show, and others, that she would never kill herself. But all his muckraking may have caught up to him. In 2011, Madsen received credible intel that his reporting had landed him square in the sights of the Obama administration, who many believe has no moral qualms over dispatching journalists challenging the status quo.
In an article published at the time, Madsen highlighted the case of investigative journalist Jack Anderson, whose reportage was a detrimental nuisance to the Nixon Administration. In describing discussions over how the pesky columnist could be assassinated, Madsen mentioned that “Staging an automobile accident in which Anderson would be incinerated was also an option,” a scenario mirroring what we may have seen played out earlier this year when Rolling Stone journalist Michael Hastings’ Merecedes burst into flames after crashing into a tree. On yesterday’s Alex Jones Show, Alex asked what the next big NSA spying revelation would be. Madsen answered that we should soon learn that the phones of high profile figures, such as the Pope, Nelson Mandela and the Dalai Lama, were also tapped, further leading the public to feel helpless under the barrage of assaults against their privacy rights. Indeed, the suppression of Madsen’s information, only to have it surface months later, shows the extent to which the establishment watches the independent media and carefully controls much of what goes out in print. In other words, Madsen’s the real deal. This article was posted: Wednesday, October 30, 2013 at 12:38 pm Tags: big brother, nsa
NSA: Not Only Snooping But Infecting Computer Networks Worldwide
Kurt Nimmo Not only does the NSA snoop your personal communications, the agency also excels at infecting computer networks with malicious software.
Edward Snowden, the former NSA analyst roundly excoriated by government as a dangerous leaker, has revealed that more than 50,000 computer networks worldwide have been infected. A management presentation shows how the surveillance agency uses “Computer Network Exploitation” (CNE) in more than 50,000 locations. “CNE is the secret infiltration of computer systems achieved by installing malware, malicious software,” reports the Dutch website, NRC.nl. The NSA has a special department dedicated to malicious hacking. Tailored Access Operation, or TAO, has more than a thousand hackers hired to go after targeted networks. In August, the Washington Post reported that TAO had installed an estimated 20,000 “implants” beginning in 2008 and by the middle of last year the number had jumped to 50,000. The implants act as “sleeper cells” that are controlled at will. “Computer hacks are relatively inexpensive and provide the NSA with opportunities to obtain information that they otherwise would not have access to,” write Floor Boon, Steven Derix and Huib Modderkolk. “The NSA-presentation shows their CNE-operations in countries such as Venezuela and Brazil. The malware installed in these countries can remain active for years without being detected.” NSA referred inquiries about the revelations to the U.S. government. A government spokesperson said the disclosure of classified information endangers U.S. national security. This article was posted: Saturday, November 23, 2013 at 11:22 am
MORE: INTERNET FALSE FLAGS
Is The NSA Quartering “Digital” Troops Within Our Homes? Are “Digital” Troops Being Sent Into Our Digital Devices Like British Troops Were Sent Into American Colonists’ Homes?
Washington’s Blog We have extensively documented that the U.S. government is trampling virtually every single Constitutional right set forth in the Bill of Rights. One of the few rights which we thought the government still respects is the the 3rd Amendment, which prohibits the government forcing people to house troops:
But security expert Jacob Appelbaum notes that the NSA may be digitally violating the 3rd Amendment. By way of background, this week Appelbaum was the main force behind an expose in Spiegel – and gave a must-watch talk – on the NSA’s systemic offensive programs to commandeer computers and computer systems, phone connections and phone systems, and communications networks of all types. Appelbaum shows that the NSA has literally taken over our computer and our phones, physically intercepting laptop shipments and installing bugware before themselves shipping the laptop on to the consumer, installing special hardware that overcomes all privacy attempts, including “air gaps” (i.e. keep a computer unplugged from the Internet). Appelbaum also notes that spyware can suck up a lot of system resources on a computer or smartphone. And he says this is the digital equivalent of soldiers being stationed in our houses against our will:
The parallel might not be as far-fetched as it may seem at first … The NSA itself says that it’s in the middle of a massive cyber war. As such, malware, physical spying devices and offensive internet workarounds are literally the main troops in the NSA’s offensive cyber army. Quartering meant that Colonial Americans had: - No control over when the British troops came and went - No say in what resources they consumed - And no privacy even in their own castles Similarly, mass NSA spying means that modern day Americans have: - No control over when military presence comes or goes from our computer and phones (NSA is part of the Department of Defense) - No say in what resources the spies suck up (remember, Applebaum says that spying can use a lot of resources and harm performance) - And no privacy even in the deepest inner sanctuary of our electronic home base Colonial Americans lost the quiet use and enjoyment of their homes. Modern Americans are losing the quiet use and enjoyment of our digital homes because the NSA is stationing digital “troops” inside our computers and phones. Just as the Colonists’ homes were no longer theirs … our computers and phones are no longer ours. This article was posted: Wednesday, January 1, 2014 at 6:21 am Tags: domestic news, domestic spying, government corruption
Only a FOOL
Washington’s Blog The NSA and other intelligence officials have been repeatedly caught lying about their spying programs.
Top terrorism and security experts also agree, saying that:
Indeed, the NSA itself no longer claims that its mass spying program has stopped terror attacks or saved lives. Instead, intelligence spokesmen themselves now claim that mass spying is just an “insurance policy” to give “peace of mind”. But given that mass surveillance by governments on their own people have always been used – for at least 500 years – to crush dissent, that the NSA has a long history of spying on Congress for political purposes, and that high-level NSA whistleblowers say that the NSA is using spying to blackmail politicians and social critics and to prosecute people the government dislikes, the question is whose peace of mind the programs preserve And while the NSA claims that disclosure of its spying programs hurts America’s security, that’s what authoritarians always say. For example:
So how can anyone believe the NSA at this point? Unfortunately, fear of terror makes people unable to think straight … and when the government undertakes a large, idiotic project – like launching the Iraq war – many people will go to great lengths to grasp at straws to try to rationalize the government’s ill-conceived campaign. The minority of Americans who believe the NSA have – sadly – fallen for the same trick … This article was posted: Tuesday, January 14, 2014 at 5:02 am Tags: constitution, domestic news, domestic spying
Tattle-Tale Squads, and SurveillanceGermans under Hitler denounced their neighbors and friends not because they genuinely believed them to be a security threat, but because they expected to selfishly benefit from doing so, both financially, socially and psychologically via a pavlovian need to be rewarded by their masters for their obedience. At the height of its influence around one in seven of the East German population was an informant for the Stasi. As in Nazi Germany, the creation of an informant system was wholly centered around identifying political dissidents and those with grievances against the state, and had little or nothing to do with genuine security concerns. LINK: Tattle-Tale Squads and Surveillance
FIGHTING
BACK!
Assembly Bill 351, commonly called the California
Liberty Preservation Act, has been signed into law by Governor Jerry Brown making it statewide policy to refuse
compliance with federal attempts to enforce "indefinite detention" made famous by the National Defense
Authorization Act of 2012 (NDAA). What began as a marginal issue with little legislative support has unified
Californians of all persuasions and brought attention to the proper role the people and their states play in a
constitutional republic.
Infowars Invades Utah 'Big Brother' Criminal Spy Center
Alex's incredible bombshell interview with Anthony Gucciardi from the NSA Data Center in Utah
where they were confronted by NSA guards who immediately violate their 1st Amendment rights and confiscated
cameras.
The Rally Against Mass Surveillance with Ben Doernberg
Alex is joined by Ben Doernberg the head of
Rally.stopwatching.us to discuss their new video fighting back against the Federal Government and NSA spying on
private citizens.
StopWatching.Us: Rally Against Mass Surveillance 10/26/13 Thousands came together in Washington, DC on October 26, 2013 to protest the NSA's mass surveillance programs.
TSA/NSA: We Will Resist Their Tyranny: 10K Film Contest
SEND YOUR LINKS TO [email protected]
How to Nullify the NSA (and every other tyrannical government agency) SHOW NOTES AND MP3: http://www.corbettreport.com/?p=8413
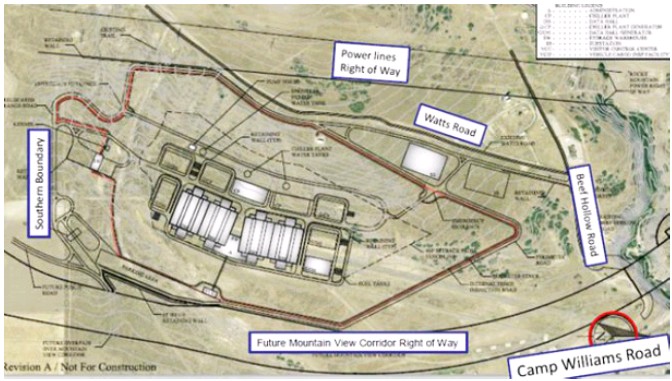
No Water = No NSA Data Center.
MORE: Fighting Back Against Big Brother
-- Harriet Tubman --
"I freed a thousand slaves; I
could have freed a thousand more,
Only the vigilant can maintain their liberties, and only those who
are constantly and intelligently "A society, most of whose members spend a great part of their time,
not on the spot, not here and now and in their calculable future, but somewhere else, in the irrelevant other
worlds of sport and soap opera, of mythology and metaphysical fantasy, will find it hard to resist the
encroachments of those who would manipulate and control it.” - Aldous Huxley - LINK: Bread and Circus
TOTAL SURVEILLANCE SOCIETY LINK: Transhumanism And The Technocratic Era
REACH OUT TO OTHERS [Help Educate Family And Friends With This Page And The Links Below]
MORE: Big Brother/Sis & Surveillance Systems | The NSA (National Security Agency) | DRONES | DHS SPY GRID | Microchip Implants | India Biometrics 1.2 Billion People | National I.D. Card | Communications Takeover by EAS | Cell Phones Are Tracking Devices | SMART METERS | 10 Reasons Why Nothing You Do On The Internet Will EVER Be Private Again CASHLESS TRACKABLE SOCIETY | Facedeals scans your face to customize deals | RFID chip Mandatory at Schools | Fighting Back Against Big Brother
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||



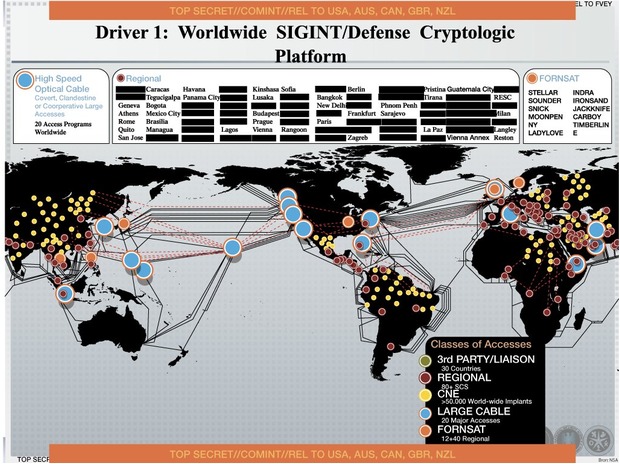
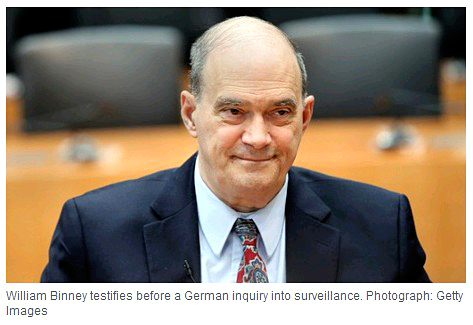 On 5 July he spoke at a
On 5 July he spoke at a  A Fisa court in 2010 allowed the NSA to spy on 193 countries around the world,
plus the World Bank, though there’s
A Fisa court in 2010 allowed the NSA to spy on 193 countries around the world,
plus the World Bank, though there’s 




















 Officials in the legislative, judicial and executive branches of government all say
that the mass surveillance on Americans is unnecessary:
Officials in the legislative, judicial and executive branches of government all say
that the mass surveillance on Americans is unnecessary: